feat:添加filebrowser、frpc、frps、home-assistant、nextcloud、hexo、zfile (#299)
17
apps/filebrowser/2.24.1/data.yml
Normal file
@ -0,0 +1,17 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: 40071
|
||||
edit: true
|
||||
envKey: PANEL_APP_PORT_HTTP
|
||||
labelEn: HTTP Port
|
||||
labelZh: HTTP端口
|
||||
required: true
|
||||
rule: paramPort
|
||||
type: number
|
||||
- default: ./data/mnt
|
||||
edit: true
|
||||
envKey: MOUNT_PATH
|
||||
labelEn: Mount folder path
|
||||
labelZh: 挂载文件夹路径
|
||||
required: true
|
||||
type: text
|
||||
8
apps/filebrowser/2.24.1/data/.filebrowser.json
Normal file
@ -0,0 +1,8 @@
|
||||
{
|
||||
"port": 80,
|
||||
"baseURL": "",
|
||||
"address": "",
|
||||
"log": "stdout",
|
||||
"database": "/database/filebrowser.db",
|
||||
"root": "/srv"
|
||||
}
|
||||
0
apps/filebrowser/2.24.1/data/database.db
Normal file
21
apps/filebrowser/2.24.1/docker-compose.yml
Normal file
@ -0,0 +1,21 @@
|
||||
version: '3'
|
||||
services:
|
||||
filebrowser:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
networks:
|
||||
- 1panel-network
|
||||
ports:
|
||||
- "${PANEL_APP_PORT_HTTP}:80"
|
||||
volumes:
|
||||
- "${MOUNT_PATH}:/srv"
|
||||
- "./data/database.db:/database.db"
|
||||
- "./data/.filebrowser.json:/.filebrowser.json"
|
||||
user: "${UID}:${GID}"
|
||||
image: filebrowser/filebrowser:v2.24.1
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
|
||||
networks:
|
||||
1panel-network:
|
||||
external: true
|
||||
44
apps/filebrowser/README.md
Normal file
@ -0,0 +1,44 @@
|
||||
# 使用说明
|
||||
|
||||
- 默认账户密码
|
||||
|
||||
```
|
||||
username:admin
|
||||
password:admin
|
||||
```
|
||||
|
||||
# 原始相关
|
||||
|
||||
<p align="center">
|
||||
<img src="https://raw.githubusercontent.com/filebrowser/logo/master/banner.png" width="550"/>
|
||||
</p>
|
||||
|
||||
|
||||
|
||||
[](https://github.com/filebrowser/filebrowser/actions/workflows/main.yaml)
|
||||
[](https://goreportcard.com/report/github.com/filebrowser/filebrowser)
|
||||
[](http://godoc.org/github.com/filebrowser/filebrowser)
|
||||
[](https://github.com/filebrowser/filebrowser/releases/latest)
|
||||
[](http://webchat.freenode.net/?channels=%23filebrowser)
|
||||
|
||||
filebrowser provides a file managing interface within a specified directory and it can be used to upload, delete, preview, rename and edit your files. It allows the creation of multiple users and each user can have its own directory. It can be used as a standalone app.
|
||||
|
||||
## Features
|
||||
|
||||
Please refer to our docs at [https://filebrowser.org/features](https://filebrowser.org/features)
|
||||
|
||||
## Install
|
||||
|
||||
For installation instructions please refer to our docs at [https://filebrowser.org/installation](https://filebrowser.org/installation).
|
||||
|
||||
## Configuration
|
||||
|
||||
[Authentication Method](https://filebrowser.org/configuration/authentication-method) - You can change the way the user authenticates with the filebrowser server
|
||||
|
||||
[Command Runner](https://filebrowser.org/configuration/command-runner) - The command runner is a feature that enables you to execute any shell command you want before or after a certain event.
|
||||
|
||||
[Custom Branding](https://filebrowser.org/configuration/custom-branding) - You can customize your File Browser installation by change its name to any other you want, by adding a global custom style sheet and by using your own logotype if you want.
|
||||
|
||||
## Contributing
|
||||
|
||||
If you're interested in contributing to this project, our docs are best places to start [https://filebrowser.org/contributing](https://filebrowser.org/contributing).
|
||||
20
apps/filebrowser/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: File Browser
|
||||
tags:
|
||||
- 工具
|
||||
title: 网页文件浏览器
|
||||
type: 工具
|
||||
description: 网页文件浏览器
|
||||
additionalProperties:
|
||||
key: filebrowser
|
||||
name: File Browser
|
||||
tags:
|
||||
- Tool
|
||||
shortDescZh: 网页文件浏览器
|
||||
shortDescEn: Web File Browser
|
||||
type: tool
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://filebrowser.org/
|
||||
github: https://github.com/filebrowser/filebrowser
|
||||
document: https://filebrowser.org/
|
||||
BIN
apps/filebrowser/logo.png
Normal file
|
After Width: | Height: | Size: 7.7 KiB |
9
apps/frpc/0.51.2/data.yml
Normal file
@ -0,0 +1,9 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: ./data/frpc.ini
|
||||
edit: false
|
||||
envKey: CONFIG_FILE_PATH
|
||||
labelEn: Configuration file path
|
||||
labelZh: 配置文件路径
|
||||
required: true
|
||||
type: text
|
||||
9
apps/frpc/0.51.2/data/frpc.ini
Normal file
@ -0,0 +1,9 @@
|
||||
[common]
|
||||
server_addr = 127.0.0.1
|
||||
server_port = 7000
|
||||
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
365
apps/frpc/0.51.2/data/frpc_full.ini
Normal file
@ -0,0 +1,365 @@
|
||||
# [common] is integral section
|
||||
[common]
|
||||
# A literal address or host name for IPv6 must be enclosed
|
||||
# in square brackets, as in "[::1]:80", "[ipv6-host]:http" or "[ipv6-host%zone]:80"
|
||||
# For single "server_addr" field, no need square brackets, like "server_addr = ::".
|
||||
server_addr = 0.0.0.0
|
||||
server_port = 7000
|
||||
|
||||
# The maximum amount of time a dial to server will wait for a connect to complete. Default value is 10 seconds.
|
||||
# dial_server_timeout = 10
|
||||
|
||||
# dial_server_keepalive specifies the interval between keep-alive probes for an active network connection between frpc and frps.
|
||||
# If negative, keep-alive probes are disabled.
|
||||
# dial_server_keepalive = 7200
|
||||
|
||||
# if you want to connect frps by http proxy or socks5 proxy or ntlm proxy, you can set http_proxy here or in global environment variables
|
||||
# it only works when protocol is tcp
|
||||
# http_proxy = http://user:passwd@192.168.1.128:8080
|
||||
# http_proxy = socks5://user:passwd@192.168.1.128:1080
|
||||
# http_proxy = ntlm://user:passwd@192.168.1.128:2080
|
||||
|
||||
# console or real logFile path like ./frpc.log
|
||||
log_file = ./frpc.log
|
||||
|
||||
# trace, debug, info, warn, error
|
||||
log_level = info
|
||||
|
||||
log_max_days = 3
|
||||
|
||||
# disable log colors when log_file is console, default is false
|
||||
disable_log_color = false
|
||||
|
||||
# for authentication, should be same as your frps.ini
|
||||
# authenticate_heartbeats specifies whether to include authentication token in heartbeats sent to frps. By default, this value is false.
|
||||
authenticate_heartbeats = false
|
||||
|
||||
# authenticate_new_work_conns specifies whether to include authentication token in new work connections sent to frps. By default, this value is false.
|
||||
authenticate_new_work_conns = false
|
||||
|
||||
# auth token
|
||||
token = 12345678
|
||||
|
||||
authentication_method =
|
||||
|
||||
# oidc_client_id specifies the client ID to use to get a token in OIDC authentication if AuthenticationMethod == "oidc".
|
||||
# By default, this value is "".
|
||||
oidc_client_id =
|
||||
|
||||
# oidc_client_secret specifies the client secret to use to get a token in OIDC authentication if AuthenticationMethod == "oidc".
|
||||
# By default, this value is "".
|
||||
oidc_client_secret =
|
||||
|
||||
# oidc_audience specifies the audience of the token in OIDC authentication if AuthenticationMethod == "oidc". By default, this value is "".
|
||||
oidc_audience =
|
||||
|
||||
# oidc_scope specifies the permisssions of the token in OIDC authentication if AuthenticationMethod == "oidc". By default, this value is "".
|
||||
oidc_scope =
|
||||
|
||||
# oidc_token_endpoint_url specifies the URL which implements OIDC Token Endpoint.
|
||||
# It will be used to get an OIDC token if AuthenticationMethod == "oidc". By default, this value is "".
|
||||
oidc_token_endpoint_url =
|
||||
|
||||
# oidc_additional_xxx specifies additional parameters to be sent to the OIDC Token Endpoint.
|
||||
# For example, if you want to specify the "audience" parameter, you can set as follow.
|
||||
# frp will add "audience=<value>" "var1=<value>" to the additional parameters.
|
||||
# oidc_additional_audience = https://dev.auth.com/api/v2/
|
||||
# oidc_additional_var1 = foobar
|
||||
|
||||
# set admin address for control frpc's action by http api such as reload
|
||||
admin_addr = 127.0.0.1
|
||||
admin_port = 7400
|
||||
admin_user = admin
|
||||
admin_pwd = admin
|
||||
# Admin assets directory. By default, these assets are bundled with frpc.
|
||||
# assets_dir = ./static
|
||||
|
||||
# connections will be established in advance, default value is zero
|
||||
pool_count = 5
|
||||
|
||||
# if tcp stream multiplexing is used, default is true, it must be same with frps
|
||||
# tcp_mux = true
|
||||
|
||||
# specify keep alive interval for tcp mux.
|
||||
# only valid if tcp_mux is true.
|
||||
# tcp_mux_keepalive_interval = 60
|
||||
|
||||
# your proxy name will be changed to {user}.{proxy}
|
||||
user = your_name
|
||||
|
||||
# decide if exit program when first login failed, otherwise continuous relogin to frps
|
||||
# default is true
|
||||
login_fail_exit = true
|
||||
|
||||
# communication protocol used to connect to server
|
||||
# supports tcp, kcp, quic and websocket now, default is tcp
|
||||
protocol = tcp
|
||||
|
||||
# set client binding ip when connect server, default is empty.
|
||||
# only when protocol = tcp or websocket, the value will be used.
|
||||
connect_server_local_ip = 0.0.0.0
|
||||
|
||||
# quic protocol options
|
||||
# quic_keepalive_period = 10
|
||||
# quic_max_idle_timeout = 30
|
||||
# quic_max_incoming_streams = 100000
|
||||
|
||||
# if tls_enable is true, frpc will connect frps by tls
|
||||
tls_enable = true
|
||||
|
||||
# tls_cert_file = client.crt
|
||||
# tls_key_file = client.key
|
||||
# tls_trusted_ca_file = ca.crt
|
||||
# tls_server_name = example.com
|
||||
|
||||
# specify a dns server, so frpc will use this instead of default one
|
||||
# dns_server = 8.8.8.8
|
||||
|
||||
# proxy names you want to start separated by ','
|
||||
# default is empty, means all proxies
|
||||
# start = ssh,dns
|
||||
|
||||
# heartbeat configure, it's not recommended to modify the default value
|
||||
# The default value of heartbeat_interval is 10 and heartbeat_timeout is 90. Set negative value
|
||||
# to disable it.
|
||||
# heartbeat_interval = 30
|
||||
# heartbeat_timeout = 90
|
||||
|
||||
# additional meta info for client
|
||||
meta_var1 = 123
|
||||
meta_var2 = 234
|
||||
|
||||
# specify udp packet size, unit is byte. If not set, the default value is 1500.
|
||||
# This parameter should be same between client and server.
|
||||
# It affects the udp and sudp proxy.
|
||||
udp_packet_size = 1500
|
||||
|
||||
# include other config files for proxies.
|
||||
# includes = ./confd/*.ini
|
||||
|
||||
# By default, frpc will connect frps with first custom byte if tls is enabled.
|
||||
# If DisableCustomTLSFirstByte is true, frpc will not send that custom byte.
|
||||
disable_custom_tls_first_byte = false
|
||||
|
||||
# Enable golang pprof handlers in admin listener.
|
||||
# Admin port must be set first.
|
||||
pprof_enable = false
|
||||
|
||||
# 'ssh' is the unique proxy name
|
||||
# if user in [common] section is not empty, it will be changed to {user}.{proxy} such as 'your_name.ssh'
|
||||
[ssh]
|
||||
# tcp | udp | http | https | stcp | xtcp, default is tcp
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
# limit bandwidth for this proxy, unit is KB and MB
|
||||
bandwidth_limit = 1MB
|
||||
# where to limit bandwidth, can be 'client' or 'server', default is 'client'
|
||||
bandwidth_limit_mode = client
|
||||
# true or false, if true, messages between frps and frpc will be encrypted, default is false
|
||||
use_encryption = false
|
||||
# if true, message will be compressed
|
||||
use_compression = false
|
||||
# remote port listen by frps
|
||||
remote_port = 6001
|
||||
# frps will load balancing connections for proxies in same group
|
||||
group = test_group
|
||||
# group should have same group key
|
||||
group_key = 123456
|
||||
# enable health check for the backend service, it support 'tcp' and 'http' now
|
||||
# frpc will connect local service's port to detect it's healthy status
|
||||
health_check_type = tcp
|
||||
# health check connection timeout
|
||||
health_check_timeout_s = 3
|
||||
# if continuous failed in 3 times, the proxy will be removed from frps
|
||||
health_check_max_failed = 3
|
||||
# every 10 seconds will do a health check
|
||||
health_check_interval_s = 10
|
||||
# additional meta info for each proxy
|
||||
meta_var1 = 123
|
||||
meta_var2 = 234
|
||||
|
||||
[ssh_random]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
# if remote_port is 0, frps will assign a random port for you
|
||||
remote_port = 0
|
||||
|
||||
# if you want to expose multiple ports, add 'range:' prefix to the section name
|
||||
# frpc will generate multiple proxies such as 'tcp_port_6010', 'tcp_port_6011' and so on.
|
||||
[range:tcp_port]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 6010-6020,6022,6024-6028
|
||||
remote_port = 6010-6020,6022,6024-6028
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[dns]
|
||||
type = udp
|
||||
local_ip = 114.114.114.114
|
||||
local_port = 53
|
||||
remote_port = 6002
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[range:udp_port]
|
||||
type = udp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 6010-6020
|
||||
remote_port = 6010-6020
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
# Resolve your domain names to [server_addr] so you can use http://web01.yourdomain.com to browse web01 and http://web02.yourdomain.com to browse web02
|
||||
[web01]
|
||||
type = http
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 80
|
||||
use_encryption = false
|
||||
use_compression = true
|
||||
# http username and password are safety certification for http protocol
|
||||
# if not set, you can access this custom_domains without certification
|
||||
http_user = admin
|
||||
http_pwd = admin
|
||||
# if domain for frps is frps.com, then you can access [web01] proxy by URL http://web01.frps.com
|
||||
subdomain = web01
|
||||
custom_domains = web01.yourdomain.com
|
||||
# locations is only available for http type
|
||||
locations = /,/pic
|
||||
# route requests to this service if http basic auto user is abc
|
||||
# route_by_http_user = abc
|
||||
host_header_rewrite = example.com
|
||||
# params with prefix "header_" will be used to update http request headers
|
||||
header_X-From-Where = frp
|
||||
health_check_type = http
|
||||
# frpc will send a GET http request '/status' to local http service
|
||||
# http service is alive when it return 2xx http response code
|
||||
health_check_url = /status
|
||||
health_check_interval_s = 10
|
||||
health_check_max_failed = 3
|
||||
health_check_timeout_s = 3
|
||||
|
||||
[web02]
|
||||
type = https
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 8000
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
subdomain = web01
|
||||
custom_domains = web02.yourdomain.com
|
||||
# if not empty, frpc will use proxy protocol to transfer connection info to your local service
|
||||
# v1 or v2 or empty
|
||||
proxy_protocol_version = v2
|
||||
|
||||
[plugin_unix_domain_socket]
|
||||
type = tcp
|
||||
remote_port = 6003
|
||||
# if plugin is defined, local_ip and local_port is useless
|
||||
# plugin will handle connections got from frps
|
||||
plugin = unix_domain_socket
|
||||
# params with prefix "plugin_" that plugin needed
|
||||
plugin_unix_path = /var/run/docker.sock
|
||||
|
||||
[plugin_http_proxy]
|
||||
type = tcp
|
||||
remote_port = 6004
|
||||
plugin = http_proxy
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
|
||||
[plugin_socks5]
|
||||
type = tcp
|
||||
remote_port = 6005
|
||||
plugin = socks5
|
||||
plugin_user = abc
|
||||
plugin_passwd = abc
|
||||
|
||||
[plugin_static_file]
|
||||
type = tcp
|
||||
remote_port = 6006
|
||||
plugin = static_file
|
||||
plugin_local_path = /var/www/blog
|
||||
plugin_strip_prefix = static
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
|
||||
[plugin_https2http]
|
||||
type = https
|
||||
custom_domains = test.yourdomain.com
|
||||
plugin = https2http
|
||||
plugin_local_addr = 127.0.0.1:80
|
||||
plugin_crt_path = ./server.crt
|
||||
plugin_key_path = ./server.key
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
|
||||
[plugin_https2https]
|
||||
type = https
|
||||
custom_domains = test.yourdomain.com
|
||||
plugin = https2https
|
||||
plugin_local_addr = 127.0.0.1:443
|
||||
plugin_crt_path = ./server.crt
|
||||
plugin_key_path = ./server.key
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
|
||||
[plugin_http2https]
|
||||
type = http
|
||||
custom_domains = test.yourdomain.com
|
||||
plugin = http2https
|
||||
plugin_local_addr = 127.0.0.1:443
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
|
||||
[secret_tcp]
|
||||
# If the type is secret tcp, remote_port is useless
|
||||
# Who want to connect local port should deploy another frpc with stcp proxy and role is visitor
|
||||
type = stcp
|
||||
# sk used for authentication for visitors
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
# user of frpc should be same in both stcp server and stcp visitor
|
||||
[secret_tcp_visitor]
|
||||
# frpc role visitor -> frps -> frpc role server
|
||||
role = visitor
|
||||
type = stcp
|
||||
# the server name you want to visitor
|
||||
server_name = secret_tcp
|
||||
sk = abcdefg
|
||||
# connect this address to visitor stcp server
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 9000
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[p2p_tcp]
|
||||
type = xtcp
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[p2p_tcp_visitor]
|
||||
role = visitor
|
||||
type = xtcp
|
||||
server_name = p2p_tcp
|
||||
sk = abcdefg
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 9001
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[tcpmuxhttpconnect]
|
||||
type = tcpmux
|
||||
multiplexer = httpconnect
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 10701
|
||||
custom_domains = tunnel1
|
||||
# route_by_http_user = user1
|
||||
2
apps/frpc/0.51.2/data/frps.ini
Normal file
@ -0,0 +1,2 @@
|
||||
[common]
|
||||
bind_port = 7000
|
||||
168
apps/frpc/0.51.2/data/frps_full.ini
Normal file
@ -0,0 +1,168 @@
|
||||
# [common] is integral section
|
||||
[common]
|
||||
# A literal address or host name for IPv6 must be enclosed
|
||||
# in square brackets, as in "[::1]:80", "[ipv6-host]:http" or "[ipv6-host%zone]:80"
|
||||
# For single "bind_addr" field, no need square brackets, like "bind_addr = ::".
|
||||
bind_addr = 0.0.0.0
|
||||
bind_port = 7000
|
||||
|
||||
# udp port to help make udp hole to penetrate nat
|
||||
bind_udp_port = 7001
|
||||
|
||||
# udp port used for kcp protocol, it can be same with 'bind_port'.
|
||||
# if not set, kcp is disabled in frps.
|
||||
kcp_bind_port = 7000
|
||||
|
||||
# udp port used for quic protocol.
|
||||
# if not set, quic is disabled in frps.
|
||||
# quic_bind_port = 7002
|
||||
# quic protocol options
|
||||
# quic_keepalive_period = 10
|
||||
# quic_max_idle_timeout = 30
|
||||
# quic_max_incoming_streams = 100000
|
||||
|
||||
# specify which address proxy will listen for, default value is same with bind_addr
|
||||
# proxy_bind_addr = 127.0.0.1
|
||||
|
||||
# if you want to support virtual host, you must set the http port for listening (optional)
|
||||
# Note: http port and https port can be same with bind_port
|
||||
vhost_http_port = 80
|
||||
vhost_https_port = 443
|
||||
|
||||
# response header timeout(seconds) for vhost http server, default is 60s
|
||||
# vhost_http_timeout = 60
|
||||
|
||||
# tcpmux_httpconnect_port specifies the port that the server listens for TCP
|
||||
# HTTP CONNECT requests. If the value is 0, the server will not multiplex TCP
|
||||
# requests on one single port. If it's not - it will listen on this value for
|
||||
# HTTP CONNECT requests. By default, this value is 0.
|
||||
# tcpmux_httpconnect_port = 1337
|
||||
|
||||
# If tcpmux_passthrough is true, frps won't do any update on traffic.
|
||||
# tcpmux_passthrough = false
|
||||
|
||||
# set dashboard_addr and dashboard_port to view dashboard of frps
|
||||
# dashboard_addr's default value is same with bind_addr
|
||||
# dashboard is available only if dashboard_port is set
|
||||
dashboard_addr = 0.0.0.0
|
||||
dashboard_port = 7500
|
||||
|
||||
# dashboard user and passwd for basic auth protect
|
||||
dashboard_user = admin
|
||||
dashboard_pwd = admin
|
||||
|
||||
# dashboard TLS mode
|
||||
dashboard_tls_mode = false
|
||||
# dashboard_tls_cert_file = server.crt
|
||||
# dashboard_tls_key_file = server.key
|
||||
|
||||
# enable_prometheus will export prometheus metrics on {dashboard_addr}:{dashboard_port} in /metrics api.
|
||||
enable_prometheus = true
|
||||
|
||||
# dashboard assets directory(only for debug mode)
|
||||
# assets_dir = ./static
|
||||
|
||||
# console or real logFile path like ./frps.log
|
||||
log_file = ./frps.log
|
||||
|
||||
# trace, debug, info, warn, error
|
||||
log_level = info
|
||||
|
||||
log_max_days = 3
|
||||
|
||||
# disable log colors when log_file is console, default is false
|
||||
disable_log_color = false
|
||||
|
||||
# DetailedErrorsToClient defines whether to send the specific error (with debug info) to frpc. By default, this value is true.
|
||||
detailed_errors_to_client = true
|
||||
|
||||
# authentication_method specifies what authentication method to use authenticate frpc with frps.
|
||||
# If "token" is specified - token will be read into login message.
|
||||
# If "oidc" is specified - OIDC (Open ID Connect) token will be issued using OIDC settings. By default, this value is "token".
|
||||
authentication_method = token
|
||||
|
||||
# authenticate_heartbeats specifies whether to include authentication token in heartbeats sent to frps. By default, this value is false.
|
||||
authenticate_heartbeats = false
|
||||
|
||||
# AuthenticateNewWorkConns specifies whether to include authentication token in new work connections sent to frps. By default, this value is false.
|
||||
authenticate_new_work_conns = false
|
||||
|
||||
# auth token
|
||||
token = 12345678
|
||||
|
||||
# oidc_issuer specifies the issuer to verify OIDC tokens with.
|
||||
# By default, this value is "".
|
||||
oidc_issuer =
|
||||
|
||||
# oidc_audience specifies the audience OIDC tokens should contain when validated.
|
||||
# By default, this value is "".
|
||||
oidc_audience =
|
||||
|
||||
# oidc_skip_expiry_check specifies whether to skip checking if the OIDC token is expired.
|
||||
# By default, this value is false.
|
||||
oidc_skip_expiry_check = false
|
||||
|
||||
# oidc_skip_issuer_check specifies whether to skip checking if the OIDC token's issuer claim matches the issuer specified in OidcIssuer.
|
||||
# By default, this value is false.
|
||||
oidc_skip_issuer_check = false
|
||||
|
||||
# heartbeat configure, it's not recommended to modify the default value
|
||||
# the default value of heartbeat_timeout is 90. Set negative value to disable it.
|
||||
# heartbeat_timeout = 90
|
||||
|
||||
# user_conn_timeout configure, it's not recommended to modify the default value
|
||||
# the default value of user_conn_timeout is 10
|
||||
# user_conn_timeout = 10
|
||||
|
||||
# only allow frpc to bind ports you list, if you set nothing, there won't be any limit
|
||||
allow_ports = 2000-3000,3001,3003,4000-50000
|
||||
|
||||
# pool_count in each proxy will change to max_pool_count if they exceed the maximum value
|
||||
max_pool_count = 5
|
||||
|
||||
# max ports can be used for each client, default value is 0 means no limit
|
||||
max_ports_per_client = 0
|
||||
|
||||
# tls_only specifies whether to only accept TLS-encrypted connections. By default, the value is false.
|
||||
tls_only = false
|
||||
|
||||
# tls_cert_file = server.crt
|
||||
# tls_key_file = server.key
|
||||
# tls_trusted_ca_file = ca.crt
|
||||
|
||||
# if subdomain_host is not empty, you can set subdomain when type is http or https in frpc's configure file
|
||||
# when subdomain is test, the host used by routing is test.frps.com
|
||||
subdomain_host = frps.com
|
||||
|
||||
# if tcp stream multiplexing is used, default is true
|
||||
# tcp_mux = true
|
||||
|
||||
# specify keep alive interval for tcp mux.
|
||||
# only valid if tcp_mux is true.
|
||||
# tcp_mux_keepalive_interval = 60
|
||||
|
||||
# tcp_keepalive specifies the interval between keep-alive probes for an active network connection between frpc and frps.
|
||||
# If negative, keep-alive probes are disabled.
|
||||
# tcp_keepalive = 7200
|
||||
|
||||
# custom 404 page for HTTP requests
|
||||
# custom_404_page = /path/to/404.html
|
||||
|
||||
# specify udp packet size, unit is byte. If not set, the default value is 1500.
|
||||
# This parameter should be same between client and server.
|
||||
# It affects the udp and sudp proxy.
|
||||
udp_packet_size = 1500
|
||||
|
||||
# Enable golang pprof handlers in dashboard listener.
|
||||
# Dashboard port must be set first
|
||||
pprof_enable = false
|
||||
|
||||
[plugin.user-manager]
|
||||
addr = 127.0.0.1:9000
|
||||
path = /handler
|
||||
ops = Login
|
||||
|
||||
[plugin.port-manager]
|
||||
addr = 127.0.0.1:9001
|
||||
path = /handler
|
||||
ops = NewProxy
|
||||
11
apps/frpc/0.51.2/docker-compose.yml
Normal file
@ -0,0 +1,11 @@
|
||||
version: "3"
|
||||
services:
|
||||
frpc:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
network_mode: "host"
|
||||
volumes:
|
||||
- "${CONFIG_FILE_PATH}:/etc/frp/frpc.ini"
|
||||
image: "snowdreamtech/frpc:0.51.2"
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
1151
apps/frpc/README.md
Normal file
@ -0,0 +1,1151 @@
|
||||
# frp
|
||||
|
||||
[](https://circleci.com/gh/fatedier/frp)
|
||||
[](https://github.com/fatedier/frp/releases)
|
||||
|
||||
[README](README.md) | [中文文档](README_zh.md)
|
||||
|
||||
<h3 align="center">Gold Sponsors</h3>
|
||||
<!--gold sponsors start-->
|
||||
<p align="center">
|
||||
<a href="https://workos.com/?utm_campaign=github_repo&utm_medium=referral&utm_content=frp&utm_source=github" target="_blank">
|
||||
<img width="350px" src="https://raw.githubusercontent.com/fatedier/frp/dev/doc/pic/sponsor_workos.png">
|
||||
</a>
|
||||
<a> </a>
|
||||
<a href="https://asocks.com/c/vDu6Dk" target="_blank">
|
||||
<img width="350px" src="https://raw.githubusercontent.com/fatedier/frp/dev/doc/pic/sponsor_asocks.jpg">
|
||||
</a>
|
||||
</p>
|
||||
|
||||
<!--gold sponsors end-->
|
||||
|
||||
## What is frp?
|
||||
|
||||
frp is a fast reverse proxy that allows you to expose a local server located behind a NAT or firewall to the Internet. It currently supports **TCP** and **UDP**, as well as **HTTP** and **HTTPS** protocols, enabling requests to be forwarded to internal services via domain name.
|
||||
|
||||
frp also offers a P2P connect mode.
|
||||
|
||||
## Table of Contents
|
||||
|
||||
<!-- vim-markdown-toc GFM -->
|
||||
|
||||
- [frp](#frp)
|
||||
- [What is frp?](#what-is-frp)
|
||||
- [Table of Contents](#table-of-contents)
|
||||
- [Development Status](#development-status)
|
||||
- [Architecture](#architecture)
|
||||
- [Example Usage](#example-usage)
|
||||
- [Access your computer in a LAN network via SSH](#access-your-computer-in-a-lan-network-via-ssh)
|
||||
- [Accessing Internal Web Services with Custom Domains in LAN](#accessing-internal-web-services-with-custom-domains-in-lan)
|
||||
- [Forward DNS query requests](#forward-dns-query-requests)
|
||||
- [Forward Unix Domain Socket](#forward-unix-domain-socket)
|
||||
- [Expose a simple HTTP file server](#expose-a-simple-http-file-server)
|
||||
- [Enable HTTPS for a local HTTP(S) service](#enable-https-for-a-local-https-service)
|
||||
- [Expose your service privately](#expose-your-service-privately)
|
||||
- [P2P Mode](#p2p-mode)
|
||||
- [Features](#features)
|
||||
- [Configuration Files](#configuration-files)
|
||||
- [Using Environment Variables](#using-environment-variables)
|
||||
- [Split Configures Into Different Files](#split-configures-into-different-files)
|
||||
- [Dashboard](#dashboard)
|
||||
- [Admin UI](#admin-ui)
|
||||
- [Monitor](#monitor)
|
||||
- [Prometheus](#prometheus)
|
||||
- [Authenticating the Client](#authenticating-the-client)
|
||||
- [Token Authentication](#token-authentication)
|
||||
- [OIDC Authentication](#oidc-authentication)
|
||||
- [Encryption and Compression](#encryption-and-compression)
|
||||
- [TLS](#tls)
|
||||
- [Hot-Reloading frpc configuration](#hot-reloading-frpc-configuration)
|
||||
- [Get proxy status from client](#get-proxy-status-from-client)
|
||||
- [Only allowing certain ports on the server](#only-allowing-certain-ports-on-the-server)
|
||||
- [Port Reuse](#port-reuse)
|
||||
- [Bandwidth Limit](#bandwidth-limit)
|
||||
- [For Each Proxy](#for-each-proxy)
|
||||
- [TCP Stream Multiplexing](#tcp-stream-multiplexing)
|
||||
- [Support KCP Protocol](#support-kcp-protocol)
|
||||
- [Support QUIC Protocol](#support-quic-protocol)
|
||||
- [Connection Pooling](#connection-pooling)
|
||||
- [Load balancing](#load-balancing)
|
||||
- [Service Health Check](#service-health-check)
|
||||
- [Rewriting the HTTP Host Header](#rewriting-the-http-host-header)
|
||||
- [Setting other HTTP Headers](#setting-other-http-headers)
|
||||
- [Get Real IP](#get-real-ip)
|
||||
- [HTTP X-Forwarded-For](#http-x-forwarded-for)
|
||||
- [Proxy Protocol](#proxy-protocol)
|
||||
- [Require HTTP Basic Auth (Password) for Web Services](#require-http-basic-auth-password-for-web-services)
|
||||
- [Custom Subdomain Names](#custom-subdomain-names)
|
||||
- [URL Routing](#url-routing)
|
||||
- [TCP Port Multiplexing](#tcp-port-multiplexing)
|
||||
- [Connecting to frps via HTTP PROXY](#connecting-to-frps-via-http-proxy)
|
||||
- [Range ports mapping](#range-ports-mapping)
|
||||
- [Client Plugins](#client-plugins)
|
||||
- [Server Manage Plugins](#server-manage-plugins)
|
||||
- [Development Plan](#development-plan)
|
||||
- [Contributing](#contributing)
|
||||
- [Donation](#donation)
|
||||
- [GitHub Sponsors](#github-sponsors)
|
||||
- [PayPal](#paypal)
|
||||
|
||||
<!-- vim-markdown-toc -->
|
||||
|
||||
## Development Status
|
||||
|
||||
frp is currently under development. You can try the latest release version in the `master` branch, or use the `dev` branch to access the version currently in development.
|
||||
|
||||
We are currently working on version 2 and attempting to perform some code refactoring and improvements. However, please note that it will not be compatible with version 1.
|
||||
|
||||
We will transition from version 0 to version 1 at the appropriate time and will only accept bug fixes and improvements, rather than big feature requests.
|
||||
|
||||
## Architecture
|
||||
|
||||
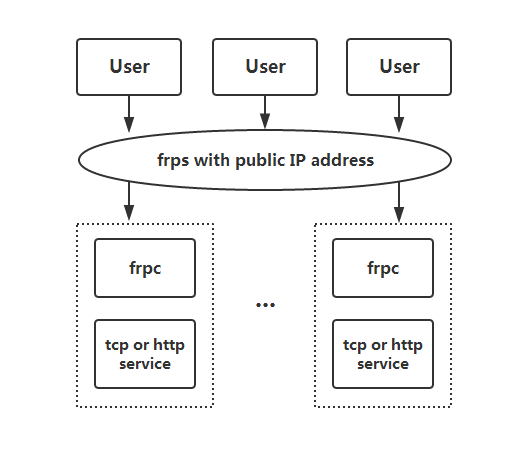
|
||||
|
||||
## Example Usage
|
||||
|
||||
To begin, download the latest program for your operating system and architecture from the [Release](https://github.com/fatedier/frp/releases) page.
|
||||
|
||||
Next, place the `frps` binary and `frps.ini` configuration file on Server A, which has a public IP address.
|
||||
|
||||
Finally, place the `frpc` binary and `frpc.ini` configuration file on Server B, which is located on a LAN that cannot be directly accessed from the public internet.
|
||||
|
||||
### Access your computer in a LAN network via SSH
|
||||
|
||||
1. Modify `frps.ini` on server A by setting the `bind_port` for frp clients to connect to:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
```
|
||||
|
||||
2. Start `frps` on server A:
|
||||
|
||||
`./frps -c ./frps.ini`
|
||||
|
||||
3. Modify `frpc.ini` on server B and set the `server_addr` field to the public IP address of your frps server:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
```
|
||||
|
||||
Note that the `local_port` (listened on the client) and `remote_port` (exposed on the server) are used for traffic going in and out of the frp system, while the `server_port` is used for communication between frps and frpc.
|
||||
|
||||
4. Start `frpc` on server B:
|
||||
|
||||
`./frpc -c ./frpc.ini`
|
||||
|
||||
5. To access server B from another machine through server A via SSH (assuming the username is `test`), use the following command:
|
||||
|
||||
`ssh -oPort=6000 test@x.x.x.x`
|
||||
|
||||
### Accessing Internal Web Services with Custom Domains in LAN
|
||||
|
||||
Sometimes we need to expose a local web service behind a NAT network to others for testing purposes with our own domain name.
|
||||
|
||||
Unfortunately, we cannot resolve a domain name to a local IP. However, we can use frp to expose an HTTP(S) service.
|
||||
|
||||
1. Modify `frps.ini` and set the HTTP port for vhost to 8080:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
vhost_http_port = 8080
|
||||
```
|
||||
|
||||
2. Start `frps`:
|
||||
|
||||
`./frps -c ./frps.ini`
|
||||
|
||||
3. Modify `frpc.ini` and set `server_addr` to the IP address of the remote frps server. Specify the `local_port` of your web service:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = www.example.com
|
||||
```
|
||||
|
||||
4. Start `frpc`:
|
||||
|
||||
`./frpc -c ./frpc.ini`
|
||||
|
||||
5. Map the A record of `www.example.com` to either the public IP of the remote frps server or a CNAME record pointing to your original domain.
|
||||
|
||||
6. Visit your local web service using url `http://www.example.com:8080`.
|
||||
|
||||
### Forward DNS query requests
|
||||
|
||||
1. Modify `frps.ini`:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
```
|
||||
|
||||
2. Start `frps`:
|
||||
|
||||
`./frps -c ./frps.ini`
|
||||
|
||||
3. Modify `frpc.ini` and set `server_addr` to the IP address of the remote frps server. Forward DNS query requests to the Google Public DNS server `8.8.8.8:53`:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[dns]
|
||||
type = udp
|
||||
local_ip = 8.8.8.8
|
||||
local_port = 53
|
||||
remote_port = 6000
|
||||
```
|
||||
|
||||
4. Start frpc:
|
||||
|
||||
`./frpc -c ./frpc.ini`
|
||||
|
||||
5. Test DNS resolution using the `dig` command:
|
||||
|
||||
`dig @x.x.x.x -p 6000 www.google.com`
|
||||
|
||||
### Forward Unix Domain Socket
|
||||
|
||||
Expose a Unix domain socket (e.g. the Docker daemon socket) as TCP.
|
||||
|
||||
Configure `frps` as above.
|
||||
|
||||
1. Start `frpc` with the following configuration:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[unix_domain_socket]
|
||||
type = tcp
|
||||
remote_port = 6000
|
||||
plugin = unix_domain_socket
|
||||
plugin_unix_path = /var/run/docker.sock
|
||||
```
|
||||
|
||||
2. Test the configuration by getting the docker version using `curl`:
|
||||
|
||||
`curl http://x.x.x.x:6000/version`
|
||||
|
||||
### Expose a simple HTTP file server
|
||||
|
||||
Expose a simple HTTP file server to access files stored in the LAN from the public Internet.
|
||||
|
||||
Configure `frps` as described above, then:
|
||||
|
||||
1. Start `frpc` with the following configuration:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[test_static_file]
|
||||
type = tcp
|
||||
remote_port = 6000
|
||||
plugin = static_file
|
||||
plugin_local_path = /tmp/files
|
||||
plugin_strip_prefix = static
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
```
|
||||
|
||||
2. Visit `http://x.x.x.x:6000/static/` from your browser and specify correct username and password to view files in `/tmp/files` on the `frpc` machine.
|
||||
|
||||
### Enable HTTPS for a local HTTP(S) service
|
||||
|
||||
You may substitute `https2https` for the plugin, and point the `plugin_local_addr` to a HTTPS endpoint.
|
||||
|
||||
1. Start `frpc` with the following configuration:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[test_https2http]
|
||||
type = https
|
||||
custom_domains = test.example.com
|
||||
|
||||
plugin = https2http
|
||||
plugin_local_addr = 127.0.0.1:80
|
||||
plugin_crt_path = ./server.crt
|
||||
plugin_key_path = ./server.key
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
```
|
||||
|
||||
2. Visit `https://test.example.com`.
|
||||
|
||||
### Expose your service privately
|
||||
|
||||
To mitigate risks associated with exposing certain services directly to the public network, STCP (Secret TCP) mode requires a preshared key to be used for access to the service from other clients.
|
||||
|
||||
Configure `frps` same as above.
|
||||
|
||||
1. Start `frpc` on machine B with the following config. This example is for exposing the SSH service (port 22), and note the `sk` field for the preshared key, and that the `remote_port` field is removed here:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[secret_ssh]
|
||||
type = stcp
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
```
|
||||
|
||||
2. Start another `frpc` (typically on another machine C) with the following config to access the SSH service with a security key (`sk` field):
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[secret_ssh_visitor]
|
||||
type = stcp
|
||||
role = visitor
|
||||
server_name = secret_ssh
|
||||
sk = abcdefg
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 6000
|
||||
```
|
||||
|
||||
3. On machine C, connect to SSH on machine B, using this command:
|
||||
|
||||
`ssh -oPort=6000 127.0.0.1`
|
||||
|
||||
### P2P Mode
|
||||
|
||||
**xtcp** is designed to transmit large amounts of data directly between clients. A frps server is still needed, as P2P here only refers to the actual data transmission.
|
||||
|
||||
Note that it may not work with all types of NAT devices. You might want to fallback to stcp if xtcp doesn't work.
|
||||
|
||||
1. In `frps.ini` configure a UDP port for xtcp:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
bind_udp_port = 7001
|
||||
```
|
||||
|
||||
2. Start `frpc` on machine B, and expose the SSH port. Note that the `remote_port` field is removed:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[p2p_ssh]
|
||||
type = xtcp
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
```
|
||||
|
||||
3. Start another `frpc` (typically on another machine C) with the configuration to connect to SSH using P2P mode:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[p2p_ssh_visitor]
|
||||
type = xtcp
|
||||
role = visitor
|
||||
server_name = p2p_ssh
|
||||
sk = abcdefg
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 6000
|
||||
```
|
||||
|
||||
4. On machine C, connect to SSH on machine B, using this command:
|
||||
|
||||
`ssh -oPort=6000 127.0.0.1`
|
||||
|
||||
## Features
|
||||
|
||||
### Configuration Files
|
||||
|
||||
Read the full example configuration files to find out even more features not described here.
|
||||
|
||||
[Full configuration file for frps (Server)](./conf/frps_full.ini)
|
||||
|
||||
[Full configuration file for frpc (Client)](./conf/frpc_full.ini)
|
||||
|
||||
### Using Environment Variables
|
||||
|
||||
Environment variables can be referenced in the configuration file, using Go's standard format:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = {{ .Envs.FRP_SERVER_ADDR }}
|
||||
server_port = 7000
|
||||
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = {{ .Envs.FRP_SSH_REMOTE_PORT }}
|
||||
```
|
||||
|
||||
With the config above, variables can be passed into `frpc` program like this:
|
||||
|
||||
```
|
||||
export FRP_SERVER_ADDR="x.x.x.x"
|
||||
export FRP_SSH_REMOTE_PORT="6000"
|
||||
./frpc -c ./frpc.ini
|
||||
```
|
||||
|
||||
`frpc` will render configuration file template using OS environment variables. Remember to prefix your reference with `.Envs`.
|
||||
|
||||
### Split Configures Into Different Files
|
||||
|
||||
You can split multiple proxy configs into different files and include them in the main file.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
includes=./confd/*.ini
|
||||
```
|
||||
|
||||
```ini
|
||||
# ./confd/test.ini
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
```
|
||||
|
||||
### Dashboard
|
||||
|
||||
Check frp's status and proxies' statistics information by Dashboard.
|
||||
|
||||
Configure a port for dashboard to enable this feature:
|
||||
|
||||
```ini
|
||||
[common]
|
||||
dashboard_port = 7500
|
||||
# dashboard's username and password are both optional
|
||||
dashboard_user = admin
|
||||
dashboard_pwd = admin
|
||||
```
|
||||
|
||||
Then visit `http://[server_addr]:7500` to see the dashboard, with username and password both being `admin`.
|
||||
|
||||
Additionally, you can use HTTPS port by using your domains wildcard or normal SSL certificate:
|
||||
|
||||
```ini
|
||||
[common]
|
||||
dashboard_port = 7500
|
||||
# dashboard's username and password are both optional
|
||||
dashboard_user = admin
|
||||
dashboard_pwd = admin
|
||||
dashboard_tls_mode = true
|
||||
dashboard_tls_cert_file = server.crt
|
||||
dashboard_tls_key_file = server.key
|
||||
```
|
||||
|
||||
Then visit `https://[server_addr]:7500` to see the dashboard in secure HTTPS connection, with username and password both being `admin`.
|
||||
|
||||
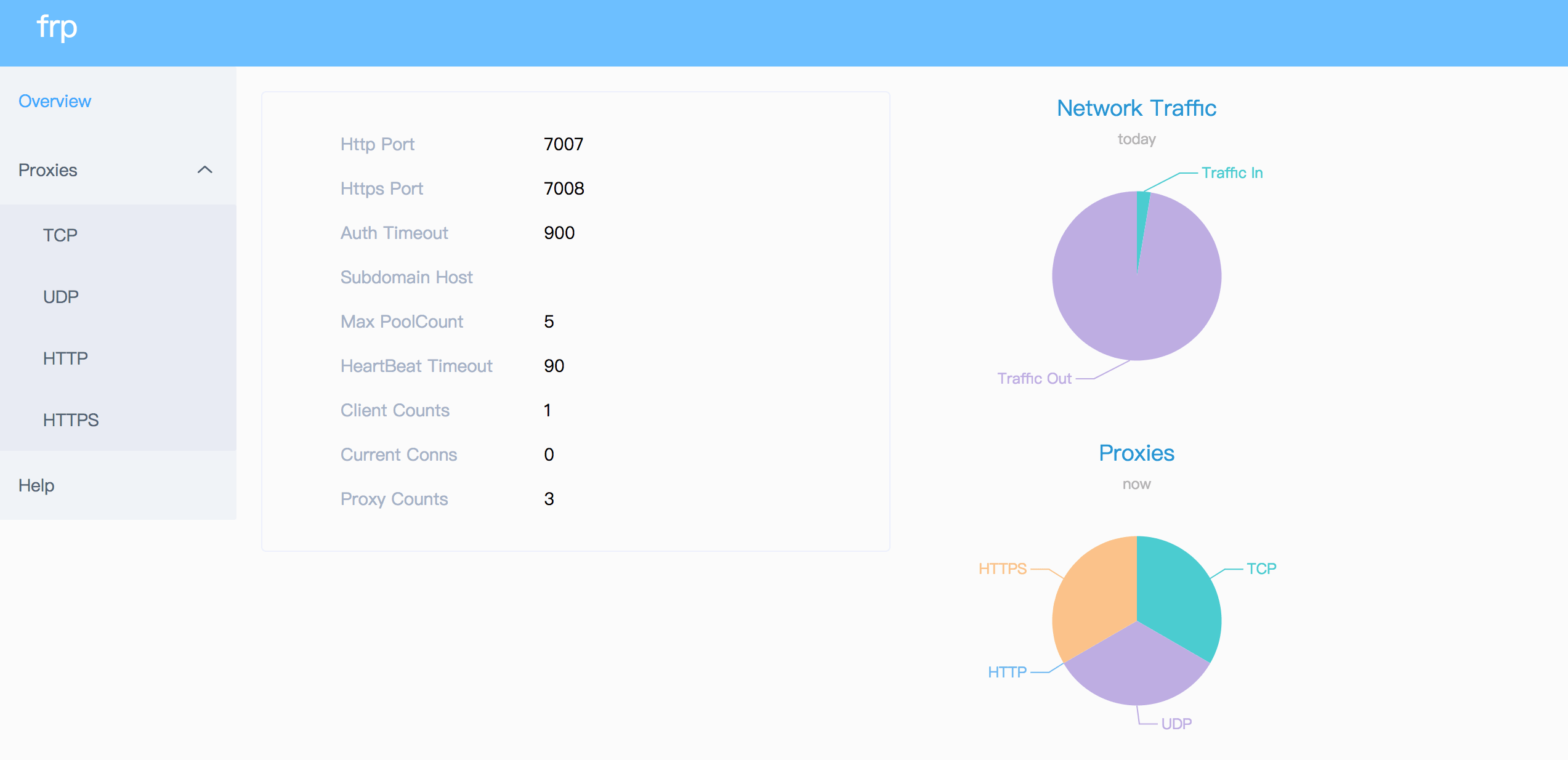
|
||||
|
||||
### Admin UI
|
||||
|
||||
The Admin UI helps you check and manage frpc's configuration.
|
||||
|
||||
Configure an address for admin UI to enable this feature:
|
||||
|
||||
```ini
|
||||
[common]
|
||||
admin_addr = 127.0.0.1
|
||||
admin_port = 7400
|
||||
admin_user = admin
|
||||
admin_pwd = admin
|
||||
```
|
||||
|
||||
Then visit `http://127.0.0.1:7400` to see admin UI, with username and password both being `admin`.
|
||||
|
||||
### Monitor
|
||||
|
||||
When dashboard is enabled, frps will save monitor data in cache. It will be cleared after process restart.
|
||||
|
||||
Prometheus is also supported.
|
||||
|
||||
#### Prometheus
|
||||
|
||||
Enable dashboard first, then configure `enable_prometheus = true` in `frps.ini`.
|
||||
|
||||
`http://{dashboard_addr}/metrics` will provide prometheus monitor data.
|
||||
|
||||
### Authenticating the Client
|
||||
|
||||
There are 2 authentication methods to authenticate frpc with frps.
|
||||
|
||||
You can decide which one to use by configuring `authentication_method` under `[common]` in `frpc.ini` and `frps.ini`.
|
||||
|
||||
Configuring `authenticate_heartbeats = true` under `[common]` will use the configured authentication method to add and validate authentication on every heartbeat between frpc and frps.
|
||||
|
||||
Configuring `authenticate_new_work_conns = true` under `[common]` will do the same for every new work connection between frpc and frps.
|
||||
|
||||
#### Token Authentication
|
||||
|
||||
When specifying `authentication_method = token` under `[common]` in `frpc.ini` and `frps.ini` - token based authentication will be used.
|
||||
|
||||
Make sure to specify the same `token` in the `[common]` section in `frps.ini` and `frpc.ini` for frpc to pass frps validation
|
||||
|
||||
#### OIDC Authentication
|
||||
|
||||
When specifying `authentication_method = oidc` under `[common]` in `frpc.ini` and `frps.ini` - OIDC based authentication will be used.
|
||||
|
||||
OIDC stands for OpenID Connect, and the flow used is called [Client Credentials Grant](https://tools.ietf.org/html/rfc6749#section-4.4).
|
||||
|
||||
To use this authentication type - configure `frpc.ini` and `frps.ini` as follows:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
authentication_method = oidc
|
||||
oidc_issuer = https://example-oidc-issuer.com/
|
||||
oidc_audience = https://oidc-audience.com/.default
|
||||
```
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
authentication_method = oidc
|
||||
oidc_client_id = 98692467-37de-409a-9fac-bb2585826f18 # Replace with OIDC client ID
|
||||
oidc_client_secret = oidc_secret
|
||||
oidc_audience = https://oidc-audience.com/.default
|
||||
oidc_token_endpoint_url = https://example-oidc-endpoint.com/oauth2/v2.0/token
|
||||
```
|
||||
|
||||
### Encryption and Compression
|
||||
|
||||
The features are off by default. You can turn on encryption and/or compression:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
use_encryption = true
|
||||
use_compression = true
|
||||
```
|
||||
|
||||
#### TLS
|
||||
|
||||
frp supports the TLS protocol between `frpc` and `frps` since v0.25.0.
|
||||
|
||||
For port multiplexing, frp sends a first byte `0x17` to dial a TLS connection.
|
||||
|
||||
Configure `tls_enable = true` in the `[common]` section to `frpc.ini` to enable this feature.
|
||||
|
||||
To **enforce** `frps` to only accept TLS connections - configure `tls_only = true` in the `[common]` section in `frps.ini`. **This is optional.**
|
||||
|
||||
**`frpc` TLS settings (under the `[common]` section):**
|
||||
```ini
|
||||
tls_enable = true
|
||||
tls_cert_file = certificate.crt
|
||||
tls_key_file = certificate.key
|
||||
tls_trusted_ca_file = ca.crt
|
||||
```
|
||||
|
||||
**`frps` TLS settings (under the `[common]` section):**
|
||||
```ini
|
||||
tls_only = true
|
||||
tls_enable = true
|
||||
tls_cert_file = certificate.crt
|
||||
tls_key_file = certificate.key
|
||||
tls_trusted_ca_file = ca.crt
|
||||
```
|
||||
|
||||
You will need **a root CA cert** and **at least one SSL/TLS certificate**. It **can** be self-signed or regular (such as Let's Encrypt or another SSL/TLS certificate provider).
|
||||
|
||||
If you using `frp` via IP address and not hostname, make sure to set the appropriate IP address in the Subject Alternative Name (SAN) area when generating SSL/TLS Certificates.
|
||||
|
||||
Given an example:
|
||||
|
||||
* Prepare openssl config file. It exists at `/etc/pki/tls/openssl.cnf` in Linux System and `/System/Library/OpenSSL/openssl.cnf` in MacOS, and you can copy it to current path, like `cp /etc/pki/tls/openssl.cnf ./my-openssl.cnf`. If not, you can build it by yourself, like:
|
||||
```
|
||||
cat > my-openssl.cnf << EOF
|
||||
[ ca ]
|
||||
default_ca = CA_default
|
||||
[ CA_default ]
|
||||
x509_extensions = usr_cert
|
||||
[ req ]
|
||||
default_bits = 2048
|
||||
default_md = sha256
|
||||
default_keyfile = privkey.pem
|
||||
distinguished_name = req_distinguished_name
|
||||
attributes = req_attributes
|
||||
x509_extensions = v3_ca
|
||||
string_mask = utf8only
|
||||
[ req_distinguished_name ]
|
||||
[ req_attributes ]
|
||||
[ usr_cert ]
|
||||
basicConstraints = CA:FALSE
|
||||
nsComment = "OpenSSL Generated Certificate"
|
||||
subjectKeyIdentifier = hash
|
||||
authorityKeyIdentifier = keyid,issuer
|
||||
[ v3_ca ]
|
||||
subjectKeyIdentifier = hash
|
||||
authorityKeyIdentifier = keyid:always,issuer
|
||||
basicConstraints = CA:true
|
||||
EOF
|
||||
```
|
||||
|
||||
* build ca certificates:
|
||||
```
|
||||
openssl genrsa -out ca.key 2048
|
||||
openssl req -x509 -new -nodes -key ca.key -subj "/CN=example.ca.com" -days 5000 -out ca.crt
|
||||
```
|
||||
|
||||
* build frps certificates:
|
||||
```
|
||||
openssl genrsa -out server.key 2048
|
||||
|
||||
openssl req -new -sha256 -key server.key \
|
||||
-subj "/C=XX/ST=DEFAULT/L=DEFAULT/O=DEFAULT/CN=server.com" \
|
||||
-reqexts SAN \
|
||||
-config <(cat my-openssl.cnf <(printf "\n[SAN]\nsubjectAltName=DNS:localhost,IP:127.0.0.1,DNS:example.server.com")) \
|
||||
-out server.csr
|
||||
|
||||
openssl x509 -req -days 365 -sha256 \
|
||||
-in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
|
||||
-extfile <(printf "subjectAltName=DNS:localhost,IP:127.0.0.1,DNS:example.server.com") \
|
||||
-out server.crt
|
||||
```
|
||||
|
||||
* build frpc certificates:
|
||||
```
|
||||
openssl genrsa -out client.key 2048
|
||||
openssl req -new -sha256 -key client.key \
|
||||
-subj "/C=XX/ST=DEFAULT/L=DEFAULT/O=DEFAULT/CN=client.com" \
|
||||
-reqexts SAN \
|
||||
-config <(cat my-openssl.cnf <(printf "\n[SAN]\nsubjectAltName=DNS:client.com,DNS:example.client.com")) \
|
||||
-out client.csr
|
||||
|
||||
openssl x509 -req -days 365 -sha256 \
|
||||
-in client.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
|
||||
-extfile <(printf "subjectAltName=DNS:client.com,DNS:example.client.com") \
|
||||
-out client.crt
|
||||
```
|
||||
|
||||
### Hot-Reloading frpc configuration
|
||||
|
||||
The `admin_addr` and `admin_port` fields are required for enabling HTTP API:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
admin_addr = 127.0.0.1
|
||||
admin_port = 7400
|
||||
```
|
||||
|
||||
Then run command `frpc reload -c ./frpc.ini` and wait for about 10 seconds to let `frpc` create or update or remove proxies.
|
||||
|
||||
**Note that parameters in [common] section won't be modified except 'start'.**
|
||||
|
||||
You can run command `frpc verify -c ./frpc.ini` before reloading to check if there are config errors.
|
||||
|
||||
### Get proxy status from client
|
||||
|
||||
Use `frpc status -c ./frpc.ini` to get status of all proxies. The `admin_addr` and `admin_port` fields are required for enabling HTTP API.
|
||||
|
||||
### Only allowing certain ports on the server
|
||||
|
||||
`allow_ports` in `frps.ini` is used to avoid abuse of ports:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
allow_ports = 2000-3000,3001,3003,4000-50000
|
||||
```
|
||||
|
||||
`allow_ports` consists of specific ports or port ranges (lowest port number, dash `-`, highest port number), separated by comma `,`.
|
||||
|
||||
### Port Reuse
|
||||
|
||||
`vhost_http_port` and `vhost_https_port` in frps can use same port with `bind_port`. frps will detect the connection's protocol and handle it correspondingly.
|
||||
|
||||
We would like to try to allow multiple proxies bind a same remote port with different protocols in the future.
|
||||
|
||||
### Bandwidth Limit
|
||||
|
||||
#### For Each Proxy
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
bandwidth_limit = 1MB
|
||||
```
|
||||
|
||||
Set `bandwidth_limit` in each proxy's configure to enable this feature. Supported units are `MB` and `KB`.
|
||||
|
||||
Set `bandwidth_limit_mode` to `client` or `server` to limit bandwidth on the client or server side. Default is `client`.
|
||||
|
||||
### TCP Stream Multiplexing
|
||||
|
||||
frp supports tcp stream multiplexing since v0.10.0 like HTTP2 Multiplexing, in which case all logic connections to the same frpc are multiplexed into the same TCP connection.
|
||||
|
||||
You can disable this feature by modify `frps.ini` and `frpc.ini`:
|
||||
|
||||
```ini
|
||||
# frps.ini and frpc.ini, must be same
|
||||
[common]
|
||||
tcp_mux = false
|
||||
```
|
||||
|
||||
### Support KCP Protocol
|
||||
|
||||
KCP is a fast and reliable protocol that can achieve the transmission effect of a reduction of the average latency by 30% to 40% and reduction of the maximum delay by a factor of three, at the cost of 10% to 20% more bandwidth wasted than TCP.
|
||||
|
||||
KCP mode uses UDP as the underlying transport. Using KCP in frp:
|
||||
|
||||
1. Enable KCP in frps:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
# Specify a UDP port for KCP.
|
||||
kcp_bind_port = 7000
|
||||
```
|
||||
|
||||
The `kcp_bind_port` number can be the same number as `bind_port`, since `bind_port` field specifies a TCP port.
|
||||
|
||||
2. Configure `frpc.ini` to use KCP to connect to frps:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
# Same as the 'kcp_bind_port' in frps.ini
|
||||
server_port = 7000
|
||||
protocol = kcp
|
||||
```
|
||||
|
||||
### Support QUIC Protocol
|
||||
|
||||
QUIC is a new multiplexed transport built on top of UDP.
|
||||
|
||||
Using QUIC in frp:
|
||||
|
||||
1. Enable QUIC in frps:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
# Specify a UDP port for QUIC.
|
||||
quic_bind_port = 7000
|
||||
```
|
||||
|
||||
The `quic_bind_port` number can be the same number as `bind_port`, since `bind_port` field specifies a TCP port.
|
||||
|
||||
2. Configure `frpc.ini` to use QUIC to connect to frps:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
# Same as the 'quic_bind_port' in frps.ini
|
||||
server_port = 7000
|
||||
protocol = quic
|
||||
```
|
||||
|
||||
### Connection Pooling
|
||||
|
||||
By default, frps creates a new frpc connection to the backend service upon a user request. With connection pooling, frps keeps a certain number of pre-established connections, reducing the time needed to establish a connection.
|
||||
|
||||
This feature is suitable for a large number of short connections.
|
||||
|
||||
1. Configure the limit of pool count each proxy can use in `frps.ini`:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
max_pool_count = 5
|
||||
```
|
||||
|
||||
2. Enable and specify the number of connection pool:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
pool_count = 1
|
||||
```
|
||||
|
||||
### Load balancing
|
||||
|
||||
Load balancing is supported by `group`.
|
||||
|
||||
This feature is only available for types `tcp`, `http`, `tcpmux` now.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[test1]
|
||||
type = tcp
|
||||
local_port = 8080
|
||||
remote_port = 80
|
||||
group = web
|
||||
group_key = 123
|
||||
|
||||
[test2]
|
||||
type = tcp
|
||||
local_port = 8081
|
||||
remote_port = 80
|
||||
group = web
|
||||
group_key = 123
|
||||
```
|
||||
|
||||
`group_key` is used for authentication.
|
||||
|
||||
Connections to port 80 will be dispatched to proxies in the same group randomly.
|
||||
|
||||
For type `tcp`, `remote_port` in the same group should be the same.
|
||||
|
||||
For type `http`, `custom_domains`, `subdomain`, `locations` should be the same.
|
||||
|
||||
### Service Health Check
|
||||
|
||||
Health check feature can help you achieve high availability with load balancing.
|
||||
|
||||
Add `health_check_type = tcp` or `health_check_type = http` to enable health check.
|
||||
|
||||
With health check type **tcp**, the service port will be pinged (TCPing):
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[test1]
|
||||
type = tcp
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
# Enable TCP health check
|
||||
health_check_type = tcp
|
||||
# TCPing timeout seconds
|
||||
health_check_timeout_s = 3
|
||||
# If health check failed 3 times in a row, the proxy will be removed from frps
|
||||
health_check_max_failed = 3
|
||||
# A health check every 10 seconds
|
||||
health_check_interval_s = 10
|
||||
```
|
||||
|
||||
With health check type **http**, an HTTP request will be sent to the service and an HTTP 2xx OK response is expected:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
# Enable HTTP health check
|
||||
health_check_type = http
|
||||
# frpc will send a GET request to '/status'
|
||||
# and expect an HTTP 2xx OK response
|
||||
health_check_url = /status
|
||||
health_check_timeout_s = 3
|
||||
health_check_max_failed = 3
|
||||
health_check_interval_s = 10
|
||||
```
|
||||
|
||||
### Rewriting the HTTP Host Header
|
||||
|
||||
By default frp does not modify the tunneled HTTP requests at all as it's a byte-for-byte copy.
|
||||
|
||||
However, speaking of web servers and HTTP requests, your web server might rely on the `Host` HTTP header to determine the website to be accessed. frp can rewrite the `Host` header when forwarding the HTTP requests, with the `host_header_rewrite` field:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
host_header_rewrite = dev.example.com
|
||||
```
|
||||
|
||||
The HTTP request will have the `Host` header rewritten to `Host: dev.example.com` when it reaches the actual web server, although the request from the browser probably has `Host: test.example.com`.
|
||||
|
||||
### Setting other HTTP Headers
|
||||
|
||||
Similar to `Host`, You can override other HTTP request headers with proxy type `http`.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
host_header_rewrite = dev.example.com
|
||||
header_X-From-Where = frp
|
||||
```
|
||||
|
||||
Note that parameter(s) prefixed with `header_` will be added to HTTP request headers.
|
||||
|
||||
In this example, it will set header `X-From-Where: frp` in the HTTP request.
|
||||
|
||||
### Get Real IP
|
||||
|
||||
#### HTTP X-Forwarded-For
|
||||
|
||||
This feature is for http proxy only.
|
||||
|
||||
You can get user's real IP from HTTP request headers `X-Forwarded-For`.
|
||||
|
||||
#### Proxy Protocol
|
||||
|
||||
frp supports Proxy Protocol to send user's real IP to local services. It support all types except UDP.
|
||||
|
||||
Here is an example for https service:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = https
|
||||
local_port = 443
|
||||
custom_domains = test.example.com
|
||||
|
||||
# now v1 and v2 are supported
|
||||
proxy_protocol_version = v2
|
||||
```
|
||||
|
||||
You can enable Proxy Protocol support in nginx to expose user's real IP in HTTP header `X-Real-IP`, and then read `X-Real-IP` header in your web service for the real IP.
|
||||
|
||||
### Require HTTP Basic Auth (Password) for Web Services
|
||||
|
||||
Anyone who can guess your tunnel URL can access your local web server unless you protect it with a password.
|
||||
|
||||
This enforces HTTP Basic Auth on all requests with the username and password specified in frpc's configure file.
|
||||
|
||||
It can only be enabled when proxy type is http.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
http_user = abc
|
||||
http_pwd = abc
|
||||
```
|
||||
|
||||
Visit `http://test.example.com` in the browser and now you are prompted to enter the username and password.
|
||||
|
||||
### Custom Subdomain Names
|
||||
|
||||
It is convenient to use `subdomain` configure for http and https types when many people share one frps server.
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
subdomain_host = frps.com
|
||||
```
|
||||
|
||||
Resolve `*.frps.com` to the frps server's IP. This is usually called a Wildcard DNS record.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
subdomain = test
|
||||
```
|
||||
|
||||
Now you can visit your web service on `test.frps.com`.
|
||||
|
||||
Note that if `subdomain_host` is not empty, `custom_domains` should not be the subdomain of `subdomain_host`.
|
||||
|
||||
### URL Routing
|
||||
|
||||
frp supports forwarding HTTP requests to different backend web services by url routing.
|
||||
|
||||
`locations` specifies the prefix of URL used for routing. frps first searches for the most specific prefix location given by literal strings regardless of the listed order.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web01]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = web.example.com
|
||||
locations = /
|
||||
|
||||
[web02]
|
||||
type = http
|
||||
local_port = 81
|
||||
custom_domains = web.example.com
|
||||
locations = /news,/about
|
||||
```
|
||||
|
||||
HTTP requests with URL prefix `/news` or `/about` will be forwarded to **web02** and other requests to **web01**.
|
||||
|
||||
### TCP Port Multiplexing
|
||||
|
||||
frp supports receiving TCP sockets directed to different proxies on a single port on frps, similar to `vhost_http_port` and `vhost_https_port`.
|
||||
|
||||
The only supported TCP port multiplexing method available at the moment is `httpconnect` - HTTP CONNECT tunnel.
|
||||
|
||||
When setting `tcpmux_httpconnect_port` to anything other than 0 in frps under `[common]`, frps will listen on this port for HTTP CONNECT requests.
|
||||
|
||||
The host of the HTTP CONNECT request will be used to match the proxy in frps. Proxy hosts can be configured in frpc by configuring `custom_domain` and / or `subdomain` under `type = tcpmux` proxies, when `multiplexer = httpconnect`.
|
||||
|
||||
For example:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
tcpmux_httpconnect_port = 1337
|
||||
```
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[proxy1]
|
||||
type = tcpmux
|
||||
multiplexer = httpconnect
|
||||
custom_domains = test1
|
||||
local_port = 80
|
||||
|
||||
[proxy2]
|
||||
type = tcpmux
|
||||
multiplexer = httpconnect
|
||||
custom_domains = test2
|
||||
local_port = 8080
|
||||
```
|
||||
|
||||
In the above configuration - frps can be contacted on port 1337 with a HTTP CONNECT header such as:
|
||||
|
||||
```
|
||||
CONNECT test1 HTTP/1.1\r\n\r\n
|
||||
```
|
||||
and the connection will be routed to `proxy1`.
|
||||
|
||||
### Connecting to frps via HTTP PROXY
|
||||
|
||||
frpc can connect to frps using HTTP proxy if you set OS environment variable `HTTP_PROXY`, or if `http_proxy` is set in frpc.ini file.
|
||||
|
||||
It only works when protocol is tcp.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
http_proxy = http://user:pwd@192.168.1.128:8080
|
||||
```
|
||||
|
||||
### Range ports mapping
|
||||
|
||||
Proxy with names that start with `range:` will support mapping range ports.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[range:test_tcp]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 6000-6006,6007
|
||||
remote_port = 6000-6006,6007
|
||||
```
|
||||
|
||||
frpc will generate 8 proxies like `test_tcp_0`, `test_tcp_1`, ..., `test_tcp_7`.
|
||||
|
||||
### Client Plugins
|
||||
|
||||
frpc only forwards requests to local TCP or UDP ports by default.
|
||||
|
||||
Plugins are used for providing rich features. There are built-in plugins such as `unix_domain_socket`, `http_proxy`, `socks5`, `static_file`, `http2https`, `https2http`, `https2https` and you can see [example usage](#example-usage).
|
||||
|
||||
Specify which plugin to use with the `plugin` parameter. Configuration parameters of plugin should be started with `plugin_`. `local_ip` and `local_port` are not used for plugin.
|
||||
|
||||
Using plugin **http_proxy**:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[http_proxy]
|
||||
type = tcp
|
||||
remote_port = 6000
|
||||
plugin = http_proxy
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
```
|
||||
|
||||
`plugin_http_user` and `plugin_http_passwd` are configuration parameters used in `http_proxy` plugin.
|
||||
|
||||
### Server Manage Plugins
|
||||
|
||||
Read the [document](/doc/server_plugin.md).
|
||||
|
||||
Find more plugins in [gofrp/plugin](https://github.com/gofrp/plugin).
|
||||
|
||||
## Development Plan
|
||||
|
||||
* Log HTTP request information in frps.
|
||||
|
||||
## Contributing
|
||||
|
||||
Interested in getting involved? We would like to help you!
|
||||
|
||||
* Take a look at our [issues list](https://github.com/fatedier/frp/issues) and consider sending a Pull Request to **dev branch**.
|
||||
* If you want to add a new feature, please create an issue first to describe the new feature, as well as the implementation approach. Once a proposal is accepted, create an implementation of the new features and submit it as a pull request.
|
||||
* Sorry for my poor English. Improvements for this document are welcome, even some typo fixes.
|
||||
* If you have great ideas, send an email to fatedier@gmail.com.
|
||||
|
||||
**Note: We prefer you to give your advise in [issues](https://github.com/fatedier/frp/issues), so others with a same question can search it quickly and we don't need to answer them repeatedly.**
|
||||
|
||||
## Donation
|
||||
|
||||
If frp helps you a lot, you can support us by:
|
||||
|
||||
### GitHub Sponsors
|
||||
|
||||
Support us by [Github Sponsors](https://github.com/sponsors/fatedier).
|
||||
|
||||
You can have your company's logo placed on README file of this project.
|
||||
|
||||
### PayPal
|
||||
|
||||
Donate money by [PayPal](https://www.paypal.me/fatedier) to my account **fatedier@gmail.com**.
|
||||
|
||||
20
apps/frpc/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: frpc-frp客户端
|
||||
tags:
|
||||
- 工具
|
||||
title: frp是一种反向代理工具,常用于内网穿透(客户端)
|
||||
type: 工具
|
||||
description: frp是一种反向代理工具,常用于内网穿透(客户端)
|
||||
additionalProperties:
|
||||
key: frpc
|
||||
name: frpc-frp客户端
|
||||
tags:
|
||||
- Tool
|
||||
shortDescZh: frp是一种反向代理工具,常用于内网穿透(客户端)
|
||||
shortDescEn: frp is a reverse proxy tool that is commonly used for intranet penetration(Client)
|
||||
type: tool
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://github.com/fatedier/frp
|
||||
github: https://github.com/fatedier/frp
|
||||
document: https://github.com/fatedier/frp/blob/dev/README_zh.md
|
||||
BIN
apps/frpc/logo.png
Normal file
|
After Width: | Height: | Size: 26 KiB |
9
apps/frps/0.51.2/data.yml
Normal file
@ -0,0 +1,9 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: ./data/frps.ini
|
||||
edit: false
|
||||
envKey: CONFIG_FILE_PATH
|
||||
labelEn: Configuration file path
|
||||
labelZh: 配置文件路径
|
||||
required: true
|
||||
type: text
|
||||
9
apps/frps/0.51.2/data/frpc.ini
Normal file
@ -0,0 +1,9 @@
|
||||
[common]
|
||||
server_addr = 127.0.0.1
|
||||
server_port = 7000
|
||||
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
365
apps/frps/0.51.2/data/frpc_full.ini
Normal file
@ -0,0 +1,365 @@
|
||||
# [common] is integral section
|
||||
[common]
|
||||
# A literal address or host name for IPv6 must be enclosed
|
||||
# in square brackets, as in "[::1]:80", "[ipv6-host]:http" or "[ipv6-host%zone]:80"
|
||||
# For single "server_addr" field, no need square brackets, like "server_addr = ::".
|
||||
server_addr = 0.0.0.0
|
||||
server_port = 7000
|
||||
|
||||
# The maximum amount of time a dial to server will wait for a connect to complete. Default value is 10 seconds.
|
||||
# dial_server_timeout = 10
|
||||
|
||||
# dial_server_keepalive specifies the interval between keep-alive probes for an active network connection between frpc and frps.
|
||||
# If negative, keep-alive probes are disabled.
|
||||
# dial_server_keepalive = 7200
|
||||
|
||||
# if you want to connect frps by http proxy or socks5 proxy or ntlm proxy, you can set http_proxy here or in global environment variables
|
||||
# it only works when protocol is tcp
|
||||
# http_proxy = http://user:passwd@192.168.1.128:8080
|
||||
# http_proxy = socks5://user:passwd@192.168.1.128:1080
|
||||
# http_proxy = ntlm://user:passwd@192.168.1.128:2080
|
||||
|
||||
# console or real logFile path like ./frpc.log
|
||||
log_file = ./frpc.log
|
||||
|
||||
# trace, debug, info, warn, error
|
||||
log_level = info
|
||||
|
||||
log_max_days = 3
|
||||
|
||||
# disable log colors when log_file is console, default is false
|
||||
disable_log_color = false
|
||||
|
||||
# for authentication, should be same as your frps.ini
|
||||
# authenticate_heartbeats specifies whether to include authentication token in heartbeats sent to frps. By default, this value is false.
|
||||
authenticate_heartbeats = false
|
||||
|
||||
# authenticate_new_work_conns specifies whether to include authentication token in new work connections sent to frps. By default, this value is false.
|
||||
authenticate_new_work_conns = false
|
||||
|
||||
# auth token
|
||||
token = 12345678
|
||||
|
||||
authentication_method =
|
||||
|
||||
# oidc_client_id specifies the client ID to use to get a token in OIDC authentication if AuthenticationMethod == "oidc".
|
||||
# By default, this value is "".
|
||||
oidc_client_id =
|
||||
|
||||
# oidc_client_secret specifies the client secret to use to get a token in OIDC authentication if AuthenticationMethod == "oidc".
|
||||
# By default, this value is "".
|
||||
oidc_client_secret =
|
||||
|
||||
# oidc_audience specifies the audience of the token in OIDC authentication if AuthenticationMethod == "oidc". By default, this value is "".
|
||||
oidc_audience =
|
||||
|
||||
# oidc_scope specifies the permisssions of the token in OIDC authentication if AuthenticationMethod == "oidc". By default, this value is "".
|
||||
oidc_scope =
|
||||
|
||||
# oidc_token_endpoint_url specifies the URL which implements OIDC Token Endpoint.
|
||||
# It will be used to get an OIDC token if AuthenticationMethod == "oidc". By default, this value is "".
|
||||
oidc_token_endpoint_url =
|
||||
|
||||
# oidc_additional_xxx specifies additional parameters to be sent to the OIDC Token Endpoint.
|
||||
# For example, if you want to specify the "audience" parameter, you can set as follow.
|
||||
# frp will add "audience=<value>" "var1=<value>" to the additional parameters.
|
||||
# oidc_additional_audience = https://dev.auth.com/api/v2/
|
||||
# oidc_additional_var1 = foobar
|
||||
|
||||
# set admin address for control frpc's action by http api such as reload
|
||||
admin_addr = 127.0.0.1
|
||||
admin_port = 7400
|
||||
admin_user = admin
|
||||
admin_pwd = admin
|
||||
# Admin assets directory. By default, these assets are bundled with frpc.
|
||||
# assets_dir = ./static
|
||||
|
||||
# connections will be established in advance, default value is zero
|
||||
pool_count = 5
|
||||
|
||||
# if tcp stream multiplexing is used, default is true, it must be same with frps
|
||||
# tcp_mux = true
|
||||
|
||||
# specify keep alive interval for tcp mux.
|
||||
# only valid if tcp_mux is true.
|
||||
# tcp_mux_keepalive_interval = 60
|
||||
|
||||
# your proxy name will be changed to {user}.{proxy}
|
||||
user = your_name
|
||||
|
||||
# decide if exit program when first login failed, otherwise continuous relogin to frps
|
||||
# default is true
|
||||
login_fail_exit = true
|
||||
|
||||
# communication protocol used to connect to server
|
||||
# supports tcp, kcp, quic and websocket now, default is tcp
|
||||
protocol = tcp
|
||||
|
||||
# set client binding ip when connect server, default is empty.
|
||||
# only when protocol = tcp or websocket, the value will be used.
|
||||
connect_server_local_ip = 0.0.0.0
|
||||
|
||||
# quic protocol options
|
||||
# quic_keepalive_period = 10
|
||||
# quic_max_idle_timeout = 30
|
||||
# quic_max_incoming_streams = 100000
|
||||
|
||||
# if tls_enable is true, frpc will connect frps by tls
|
||||
tls_enable = true
|
||||
|
||||
# tls_cert_file = client.crt
|
||||
# tls_key_file = client.key
|
||||
# tls_trusted_ca_file = ca.crt
|
||||
# tls_server_name = example.com
|
||||
|
||||
# specify a dns server, so frpc will use this instead of default one
|
||||
# dns_server = 8.8.8.8
|
||||
|
||||
# proxy names you want to start separated by ','
|
||||
# default is empty, means all proxies
|
||||
# start = ssh,dns
|
||||
|
||||
# heartbeat configure, it's not recommended to modify the default value
|
||||
# The default value of heartbeat_interval is 10 and heartbeat_timeout is 90. Set negative value
|
||||
# to disable it.
|
||||
# heartbeat_interval = 30
|
||||
# heartbeat_timeout = 90
|
||||
|
||||
# additional meta info for client
|
||||
meta_var1 = 123
|
||||
meta_var2 = 234
|
||||
|
||||
# specify udp packet size, unit is byte. If not set, the default value is 1500.
|
||||
# This parameter should be same between client and server.
|
||||
# It affects the udp and sudp proxy.
|
||||
udp_packet_size = 1500
|
||||
|
||||
# include other config files for proxies.
|
||||
# includes = ./confd/*.ini
|
||||
|
||||
# By default, frpc will connect frps with first custom byte if tls is enabled.
|
||||
# If DisableCustomTLSFirstByte is true, frpc will not send that custom byte.
|
||||
disable_custom_tls_first_byte = false
|
||||
|
||||
# Enable golang pprof handlers in admin listener.
|
||||
# Admin port must be set first.
|
||||
pprof_enable = false
|
||||
|
||||
# 'ssh' is the unique proxy name
|
||||
# if user in [common] section is not empty, it will be changed to {user}.{proxy} such as 'your_name.ssh'
|
||||
[ssh]
|
||||
# tcp | udp | http | https | stcp | xtcp, default is tcp
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
# limit bandwidth for this proxy, unit is KB and MB
|
||||
bandwidth_limit = 1MB
|
||||
# where to limit bandwidth, can be 'client' or 'server', default is 'client'
|
||||
bandwidth_limit_mode = client
|
||||
# true or false, if true, messages between frps and frpc will be encrypted, default is false
|
||||
use_encryption = false
|
||||
# if true, message will be compressed
|
||||
use_compression = false
|
||||
# remote port listen by frps
|
||||
remote_port = 6001
|
||||
# frps will load balancing connections for proxies in same group
|
||||
group = test_group
|
||||
# group should have same group key
|
||||
group_key = 123456
|
||||
# enable health check for the backend service, it support 'tcp' and 'http' now
|
||||
# frpc will connect local service's port to detect it's healthy status
|
||||
health_check_type = tcp
|
||||
# health check connection timeout
|
||||
health_check_timeout_s = 3
|
||||
# if continuous failed in 3 times, the proxy will be removed from frps
|
||||
health_check_max_failed = 3
|
||||
# every 10 seconds will do a health check
|
||||
health_check_interval_s = 10
|
||||
# additional meta info for each proxy
|
||||
meta_var1 = 123
|
||||
meta_var2 = 234
|
||||
|
||||
[ssh_random]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
# if remote_port is 0, frps will assign a random port for you
|
||||
remote_port = 0
|
||||
|
||||
# if you want to expose multiple ports, add 'range:' prefix to the section name
|
||||
# frpc will generate multiple proxies such as 'tcp_port_6010', 'tcp_port_6011' and so on.
|
||||
[range:tcp_port]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 6010-6020,6022,6024-6028
|
||||
remote_port = 6010-6020,6022,6024-6028
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[dns]
|
||||
type = udp
|
||||
local_ip = 114.114.114.114
|
||||
local_port = 53
|
||||
remote_port = 6002
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[range:udp_port]
|
||||
type = udp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 6010-6020
|
||||
remote_port = 6010-6020
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
# Resolve your domain names to [server_addr] so you can use http://web01.yourdomain.com to browse web01 and http://web02.yourdomain.com to browse web02
|
||||
[web01]
|
||||
type = http
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 80
|
||||
use_encryption = false
|
||||
use_compression = true
|
||||
# http username and password are safety certification for http protocol
|
||||
# if not set, you can access this custom_domains without certification
|
||||
http_user = admin
|
||||
http_pwd = admin
|
||||
# if domain for frps is frps.com, then you can access [web01] proxy by URL http://web01.frps.com
|
||||
subdomain = web01
|
||||
custom_domains = web01.yourdomain.com
|
||||
# locations is only available for http type
|
||||
locations = /,/pic
|
||||
# route requests to this service if http basic auto user is abc
|
||||
# route_by_http_user = abc
|
||||
host_header_rewrite = example.com
|
||||
# params with prefix "header_" will be used to update http request headers
|
||||
header_X-From-Where = frp
|
||||
health_check_type = http
|
||||
# frpc will send a GET http request '/status' to local http service
|
||||
# http service is alive when it return 2xx http response code
|
||||
health_check_url = /status
|
||||
health_check_interval_s = 10
|
||||
health_check_max_failed = 3
|
||||
health_check_timeout_s = 3
|
||||
|
||||
[web02]
|
||||
type = https
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 8000
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
subdomain = web01
|
||||
custom_domains = web02.yourdomain.com
|
||||
# if not empty, frpc will use proxy protocol to transfer connection info to your local service
|
||||
# v1 or v2 or empty
|
||||
proxy_protocol_version = v2
|
||||
|
||||
[plugin_unix_domain_socket]
|
||||
type = tcp
|
||||
remote_port = 6003
|
||||
# if plugin is defined, local_ip and local_port is useless
|
||||
# plugin will handle connections got from frps
|
||||
plugin = unix_domain_socket
|
||||
# params with prefix "plugin_" that plugin needed
|
||||
plugin_unix_path = /var/run/docker.sock
|
||||
|
||||
[plugin_http_proxy]
|
||||
type = tcp
|
||||
remote_port = 6004
|
||||
plugin = http_proxy
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
|
||||
[plugin_socks5]
|
||||
type = tcp
|
||||
remote_port = 6005
|
||||
plugin = socks5
|
||||
plugin_user = abc
|
||||
plugin_passwd = abc
|
||||
|
||||
[plugin_static_file]
|
||||
type = tcp
|
||||
remote_port = 6006
|
||||
plugin = static_file
|
||||
plugin_local_path = /var/www/blog
|
||||
plugin_strip_prefix = static
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
|
||||
[plugin_https2http]
|
||||
type = https
|
||||
custom_domains = test.yourdomain.com
|
||||
plugin = https2http
|
||||
plugin_local_addr = 127.0.0.1:80
|
||||
plugin_crt_path = ./server.crt
|
||||
plugin_key_path = ./server.key
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
|
||||
[plugin_https2https]
|
||||
type = https
|
||||
custom_domains = test.yourdomain.com
|
||||
plugin = https2https
|
||||
plugin_local_addr = 127.0.0.1:443
|
||||
plugin_crt_path = ./server.crt
|
||||
plugin_key_path = ./server.key
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
|
||||
[plugin_http2https]
|
||||
type = http
|
||||
custom_domains = test.yourdomain.com
|
||||
plugin = http2https
|
||||
plugin_local_addr = 127.0.0.1:443
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
|
||||
[secret_tcp]
|
||||
# If the type is secret tcp, remote_port is useless
|
||||
# Who want to connect local port should deploy another frpc with stcp proxy and role is visitor
|
||||
type = stcp
|
||||
# sk used for authentication for visitors
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
# user of frpc should be same in both stcp server and stcp visitor
|
||||
[secret_tcp_visitor]
|
||||
# frpc role visitor -> frps -> frpc role server
|
||||
role = visitor
|
||||
type = stcp
|
||||
# the server name you want to visitor
|
||||
server_name = secret_tcp
|
||||
sk = abcdefg
|
||||
# connect this address to visitor stcp server
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 9000
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[p2p_tcp]
|
||||
type = xtcp
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[p2p_tcp_visitor]
|
||||
role = visitor
|
||||
type = xtcp
|
||||
server_name = p2p_tcp
|
||||
sk = abcdefg
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 9001
|
||||
use_encryption = false
|
||||
use_compression = false
|
||||
|
||||
[tcpmuxhttpconnect]
|
||||
type = tcpmux
|
||||
multiplexer = httpconnect
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 10701
|
||||
custom_domains = tunnel1
|
||||
# route_by_http_user = user1
|
||||
2
apps/frps/0.51.2/data/frps.ini
Normal file
@ -0,0 +1,2 @@
|
||||
[common]
|
||||
bind_port = 7000
|
||||
168
apps/frps/0.51.2/data/frps_full.ini
Normal file
@ -0,0 +1,168 @@
|
||||
# [common] is integral section
|
||||
[common]
|
||||
# A literal address or host name for IPv6 must be enclosed
|
||||
# in square brackets, as in "[::1]:80", "[ipv6-host]:http" or "[ipv6-host%zone]:80"
|
||||
# For single "bind_addr" field, no need square brackets, like "bind_addr = ::".
|
||||
bind_addr = 0.0.0.0
|
||||
bind_port = 7000
|
||||
|
||||
# udp port to help make udp hole to penetrate nat
|
||||
bind_udp_port = 7001
|
||||
|
||||
# udp port used for kcp protocol, it can be same with 'bind_port'.
|
||||
# if not set, kcp is disabled in frps.
|
||||
kcp_bind_port = 7000
|
||||
|
||||
# udp port used for quic protocol.
|
||||
# if not set, quic is disabled in frps.
|
||||
# quic_bind_port = 7002
|
||||
# quic protocol options
|
||||
# quic_keepalive_period = 10
|
||||
# quic_max_idle_timeout = 30
|
||||
# quic_max_incoming_streams = 100000
|
||||
|
||||
# specify which address proxy will listen for, default value is same with bind_addr
|
||||
# proxy_bind_addr = 127.0.0.1
|
||||
|
||||
# if you want to support virtual host, you must set the http port for listening (optional)
|
||||
# Note: http port and https port can be same with bind_port
|
||||
vhost_http_port = 80
|
||||
vhost_https_port = 443
|
||||
|
||||
# response header timeout(seconds) for vhost http server, default is 60s
|
||||
# vhost_http_timeout = 60
|
||||
|
||||
# tcpmux_httpconnect_port specifies the port that the server listens for TCP
|
||||
# HTTP CONNECT requests. If the value is 0, the server will not multiplex TCP
|
||||
# requests on one single port. If it's not - it will listen on this value for
|
||||
# HTTP CONNECT requests. By default, this value is 0.
|
||||
# tcpmux_httpconnect_port = 1337
|
||||
|
||||
# If tcpmux_passthrough is true, frps won't do any update on traffic.
|
||||
# tcpmux_passthrough = false
|
||||
|
||||
# set dashboard_addr and dashboard_port to view dashboard of frps
|
||||
# dashboard_addr's default value is same with bind_addr
|
||||
# dashboard is available only if dashboard_port is set
|
||||
dashboard_addr = 0.0.0.0
|
||||
dashboard_port = 7500
|
||||
|
||||
# dashboard user and passwd for basic auth protect
|
||||
dashboard_user = admin
|
||||
dashboard_pwd = admin
|
||||
|
||||
# dashboard TLS mode
|
||||
dashboard_tls_mode = false
|
||||
# dashboard_tls_cert_file = server.crt
|
||||
# dashboard_tls_key_file = server.key
|
||||
|
||||
# enable_prometheus will export prometheus metrics on {dashboard_addr}:{dashboard_port} in /metrics api.
|
||||
enable_prometheus = true
|
||||
|
||||
# dashboard assets directory(only for debug mode)
|
||||
# assets_dir = ./static
|
||||
|
||||
# console or real logFile path like ./frps.log
|
||||
log_file = ./frps.log
|
||||
|
||||
# trace, debug, info, warn, error
|
||||
log_level = info
|
||||
|
||||
log_max_days = 3
|
||||
|
||||
# disable log colors when log_file is console, default is false
|
||||
disable_log_color = false
|
||||
|
||||
# DetailedErrorsToClient defines whether to send the specific error (with debug info) to frpc. By default, this value is true.
|
||||
detailed_errors_to_client = true
|
||||
|
||||
# authentication_method specifies what authentication method to use authenticate frpc with frps.
|
||||
# If "token" is specified - token will be read into login message.
|
||||
# If "oidc" is specified - OIDC (Open ID Connect) token will be issued using OIDC settings. By default, this value is "token".
|
||||
authentication_method = token
|
||||
|
||||
# authenticate_heartbeats specifies whether to include authentication token in heartbeats sent to frps. By default, this value is false.
|
||||
authenticate_heartbeats = false
|
||||
|
||||
# AuthenticateNewWorkConns specifies whether to include authentication token in new work connections sent to frps. By default, this value is false.
|
||||
authenticate_new_work_conns = false
|
||||
|
||||
# auth token
|
||||
token = 12345678
|
||||
|
||||
# oidc_issuer specifies the issuer to verify OIDC tokens with.
|
||||
# By default, this value is "".
|
||||
oidc_issuer =
|
||||
|
||||
# oidc_audience specifies the audience OIDC tokens should contain when validated.
|
||||
# By default, this value is "".
|
||||
oidc_audience =
|
||||
|
||||
# oidc_skip_expiry_check specifies whether to skip checking if the OIDC token is expired.
|
||||
# By default, this value is false.
|
||||
oidc_skip_expiry_check = false
|
||||
|
||||
# oidc_skip_issuer_check specifies whether to skip checking if the OIDC token's issuer claim matches the issuer specified in OidcIssuer.
|
||||
# By default, this value is false.
|
||||
oidc_skip_issuer_check = false
|
||||
|
||||
# heartbeat configure, it's not recommended to modify the default value
|
||||
# the default value of heartbeat_timeout is 90. Set negative value to disable it.
|
||||
# heartbeat_timeout = 90
|
||||
|
||||
# user_conn_timeout configure, it's not recommended to modify the default value
|
||||
# the default value of user_conn_timeout is 10
|
||||
# user_conn_timeout = 10
|
||||
|
||||
# only allow frpc to bind ports you list, if you set nothing, there won't be any limit
|
||||
allow_ports = 2000-3000,3001,3003,4000-50000
|
||||
|
||||
# pool_count in each proxy will change to max_pool_count if they exceed the maximum value
|
||||
max_pool_count = 5
|
||||
|
||||
# max ports can be used for each client, default value is 0 means no limit
|
||||
max_ports_per_client = 0
|
||||
|
||||
# tls_only specifies whether to only accept TLS-encrypted connections. By default, the value is false.
|
||||
tls_only = false
|
||||
|
||||
# tls_cert_file = server.crt
|
||||
# tls_key_file = server.key
|
||||
# tls_trusted_ca_file = ca.crt
|
||||
|
||||
# if subdomain_host is not empty, you can set subdomain when type is http or https in frpc's configure file
|
||||
# when subdomain is test, the host used by routing is test.frps.com
|
||||
subdomain_host = frps.com
|
||||
|
||||
# if tcp stream multiplexing is used, default is true
|
||||
# tcp_mux = true
|
||||
|
||||
# specify keep alive interval for tcp mux.
|
||||
# only valid if tcp_mux is true.
|
||||
# tcp_mux_keepalive_interval = 60
|
||||
|
||||
# tcp_keepalive specifies the interval between keep-alive probes for an active network connection between frpc and frps.
|
||||
# If negative, keep-alive probes are disabled.
|
||||
# tcp_keepalive = 7200
|
||||
|
||||
# custom 404 page for HTTP requests
|
||||
# custom_404_page = /path/to/404.html
|
||||
|
||||
# specify udp packet size, unit is byte. If not set, the default value is 1500.
|
||||
# This parameter should be same between client and server.
|
||||
# It affects the udp and sudp proxy.
|
||||
udp_packet_size = 1500
|
||||
|
||||
# Enable golang pprof handlers in dashboard listener.
|
||||
# Dashboard port must be set first
|
||||
pprof_enable = false
|
||||
|
||||
[plugin.user-manager]
|
||||
addr = 127.0.0.1:9000
|
||||
path = /handler
|
||||
ops = Login
|
||||
|
||||
[plugin.port-manager]
|
||||
addr = 127.0.0.1:9001
|
||||
path = /handler
|
||||
ops = NewProxy
|
||||
11
apps/frps/0.51.2/docker-compose.yml
Normal file
@ -0,0 +1,11 @@
|
||||
version: "3"
|
||||
services:
|
||||
frps:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
network_mode: "host"
|
||||
volumes:
|
||||
- "${CONFIG_FILE_PATH}:/etc/frp/frps.ini"
|
||||
image: "snowdreamtech/frps:0.51.2"
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
1151
apps/frps/README.md
Normal file
@ -0,0 +1,1151 @@
|
||||
# frp
|
||||
|
||||
[](https://circleci.com/gh/fatedier/frp)
|
||||
[](https://github.com/fatedier/frp/releases)
|
||||
|
||||
[README](README.md) | [中文文档](README_zh.md)
|
||||
|
||||
<h3 align="center">Gold Sponsors</h3>
|
||||
<!--gold sponsors start-->
|
||||
<p align="center">
|
||||
<a href="https://workos.com/?utm_campaign=github_repo&utm_medium=referral&utm_content=frp&utm_source=github" target="_blank">
|
||||
<img width="350px" src="https://raw.githubusercontent.com/fatedier/frp/dev/doc/pic/sponsor_workos.png">
|
||||
</a>
|
||||
<a> </a>
|
||||
<a href="https://asocks.com/c/vDu6Dk" target="_blank">
|
||||
<img width="350px" src="https://raw.githubusercontent.com/fatedier/frp/dev/doc/pic/sponsor_asocks.jpg">
|
||||
</a>
|
||||
</p>
|
||||
|
||||
<!--gold sponsors end-->
|
||||
|
||||
## What is frp?
|
||||
|
||||
frp is a fast reverse proxy that allows you to expose a local server located behind a NAT or firewall to the Internet. It currently supports **TCP** and **UDP**, as well as **HTTP** and **HTTPS** protocols, enabling requests to be forwarded to internal services via domain name.
|
||||
|
||||
frp also offers a P2P connect mode.
|
||||
|
||||
## Table of Contents
|
||||
|
||||
<!-- vim-markdown-toc GFM -->
|
||||
|
||||
- [frp](#frp)
|
||||
- [What is frp?](#what-is-frp)
|
||||
- [Table of Contents](#table-of-contents)
|
||||
- [Development Status](#development-status)
|
||||
- [Architecture](#architecture)
|
||||
- [Example Usage](#example-usage)
|
||||
- [Access your computer in a LAN network via SSH](#access-your-computer-in-a-lan-network-via-ssh)
|
||||
- [Accessing Internal Web Services with Custom Domains in LAN](#accessing-internal-web-services-with-custom-domains-in-lan)
|
||||
- [Forward DNS query requests](#forward-dns-query-requests)
|
||||
- [Forward Unix Domain Socket](#forward-unix-domain-socket)
|
||||
- [Expose a simple HTTP file server](#expose-a-simple-http-file-server)
|
||||
- [Enable HTTPS for a local HTTP(S) service](#enable-https-for-a-local-https-service)
|
||||
- [Expose your service privately](#expose-your-service-privately)
|
||||
- [P2P Mode](#p2p-mode)
|
||||
- [Features](#features)
|
||||
- [Configuration Files](#configuration-files)
|
||||
- [Using Environment Variables](#using-environment-variables)
|
||||
- [Split Configures Into Different Files](#split-configures-into-different-files)
|
||||
- [Dashboard](#dashboard)
|
||||
- [Admin UI](#admin-ui)
|
||||
- [Monitor](#monitor)
|
||||
- [Prometheus](#prometheus)
|
||||
- [Authenticating the Client](#authenticating-the-client)
|
||||
- [Token Authentication](#token-authentication)
|
||||
- [OIDC Authentication](#oidc-authentication)
|
||||
- [Encryption and Compression](#encryption-and-compression)
|
||||
- [TLS](#tls)
|
||||
- [Hot-Reloading frpc configuration](#hot-reloading-frpc-configuration)
|
||||
- [Get proxy status from client](#get-proxy-status-from-client)
|
||||
- [Only allowing certain ports on the server](#only-allowing-certain-ports-on-the-server)
|
||||
- [Port Reuse](#port-reuse)
|
||||
- [Bandwidth Limit](#bandwidth-limit)
|
||||
- [For Each Proxy](#for-each-proxy)
|
||||
- [TCP Stream Multiplexing](#tcp-stream-multiplexing)
|
||||
- [Support KCP Protocol](#support-kcp-protocol)
|
||||
- [Support QUIC Protocol](#support-quic-protocol)
|
||||
- [Connection Pooling](#connection-pooling)
|
||||
- [Load balancing](#load-balancing)
|
||||
- [Service Health Check](#service-health-check)
|
||||
- [Rewriting the HTTP Host Header](#rewriting-the-http-host-header)
|
||||
- [Setting other HTTP Headers](#setting-other-http-headers)
|
||||
- [Get Real IP](#get-real-ip)
|
||||
- [HTTP X-Forwarded-For](#http-x-forwarded-for)
|
||||
- [Proxy Protocol](#proxy-protocol)
|
||||
- [Require HTTP Basic Auth (Password) for Web Services](#require-http-basic-auth-password-for-web-services)
|
||||
- [Custom Subdomain Names](#custom-subdomain-names)
|
||||
- [URL Routing](#url-routing)
|
||||
- [TCP Port Multiplexing](#tcp-port-multiplexing)
|
||||
- [Connecting to frps via HTTP PROXY](#connecting-to-frps-via-http-proxy)
|
||||
- [Range ports mapping](#range-ports-mapping)
|
||||
- [Client Plugins](#client-plugins)
|
||||
- [Server Manage Plugins](#server-manage-plugins)
|
||||
- [Development Plan](#development-plan)
|
||||
- [Contributing](#contributing)
|
||||
- [Donation](#donation)
|
||||
- [GitHub Sponsors](#github-sponsors)
|
||||
- [PayPal](#paypal)
|
||||
|
||||
<!-- vim-markdown-toc -->
|
||||
|
||||
## Development Status
|
||||
|
||||
frp is currently under development. You can try the latest release version in the `master` branch, or use the `dev` branch to access the version currently in development.
|
||||
|
||||
We are currently working on version 2 and attempting to perform some code refactoring and improvements. However, please note that it will not be compatible with version 1.
|
||||
|
||||
We will transition from version 0 to version 1 at the appropriate time and will only accept bug fixes and improvements, rather than big feature requests.
|
||||
|
||||
## Architecture
|
||||
|
||||

|
||||
|
||||
## Example Usage
|
||||
|
||||
To begin, download the latest program for your operating system and architecture from the [Release](https://github.com/fatedier/frp/releases) page.
|
||||
|
||||
Next, place the `frps` binary and `frps.ini` configuration file on Server A, which has a public IP address.
|
||||
|
||||
Finally, place the `frpc` binary and `frpc.ini` configuration file on Server B, which is located on a LAN that cannot be directly accessed from the public internet.
|
||||
|
||||
### Access your computer in a LAN network via SSH
|
||||
|
||||
1. Modify `frps.ini` on server A by setting the `bind_port` for frp clients to connect to:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
```
|
||||
|
||||
2. Start `frps` on server A:
|
||||
|
||||
`./frps -c ./frps.ini`
|
||||
|
||||
3. Modify `frpc.ini` on server B and set the `server_addr` field to the public IP address of your frps server:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
```
|
||||
|
||||
Note that the `local_port` (listened on the client) and `remote_port` (exposed on the server) are used for traffic going in and out of the frp system, while the `server_port` is used for communication between frps and frpc.
|
||||
|
||||
4. Start `frpc` on server B:
|
||||
|
||||
`./frpc -c ./frpc.ini`
|
||||
|
||||
5. To access server B from another machine through server A via SSH (assuming the username is `test`), use the following command:
|
||||
|
||||
`ssh -oPort=6000 test@x.x.x.x`
|
||||
|
||||
### Accessing Internal Web Services with Custom Domains in LAN
|
||||
|
||||
Sometimes we need to expose a local web service behind a NAT network to others for testing purposes with our own domain name.
|
||||
|
||||
Unfortunately, we cannot resolve a domain name to a local IP. However, we can use frp to expose an HTTP(S) service.
|
||||
|
||||
1. Modify `frps.ini` and set the HTTP port for vhost to 8080:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
vhost_http_port = 8080
|
||||
```
|
||||
|
||||
2. Start `frps`:
|
||||
|
||||
`./frps -c ./frps.ini`
|
||||
|
||||
3. Modify `frpc.ini` and set `server_addr` to the IP address of the remote frps server. Specify the `local_port` of your web service:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = www.example.com
|
||||
```
|
||||
|
||||
4. Start `frpc`:
|
||||
|
||||
`./frpc -c ./frpc.ini`
|
||||
|
||||
5. Map the A record of `www.example.com` to either the public IP of the remote frps server or a CNAME record pointing to your original domain.
|
||||
|
||||
6. Visit your local web service using url `http://www.example.com:8080`.
|
||||
|
||||
### Forward DNS query requests
|
||||
|
||||
1. Modify `frps.ini`:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
```
|
||||
|
||||
2. Start `frps`:
|
||||
|
||||
`./frps -c ./frps.ini`
|
||||
|
||||
3. Modify `frpc.ini` and set `server_addr` to the IP address of the remote frps server. Forward DNS query requests to the Google Public DNS server `8.8.8.8:53`:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[dns]
|
||||
type = udp
|
||||
local_ip = 8.8.8.8
|
||||
local_port = 53
|
||||
remote_port = 6000
|
||||
```
|
||||
|
||||
4. Start frpc:
|
||||
|
||||
`./frpc -c ./frpc.ini`
|
||||
|
||||
5. Test DNS resolution using the `dig` command:
|
||||
|
||||
`dig @x.x.x.x -p 6000 www.google.com`
|
||||
|
||||
### Forward Unix Domain Socket
|
||||
|
||||
Expose a Unix domain socket (e.g. the Docker daemon socket) as TCP.
|
||||
|
||||
Configure `frps` as above.
|
||||
|
||||
1. Start `frpc` with the following configuration:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[unix_domain_socket]
|
||||
type = tcp
|
||||
remote_port = 6000
|
||||
plugin = unix_domain_socket
|
||||
plugin_unix_path = /var/run/docker.sock
|
||||
```
|
||||
|
||||
2. Test the configuration by getting the docker version using `curl`:
|
||||
|
||||
`curl http://x.x.x.x:6000/version`
|
||||
|
||||
### Expose a simple HTTP file server
|
||||
|
||||
Expose a simple HTTP file server to access files stored in the LAN from the public Internet.
|
||||
|
||||
Configure `frps` as described above, then:
|
||||
|
||||
1. Start `frpc` with the following configuration:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[test_static_file]
|
||||
type = tcp
|
||||
remote_port = 6000
|
||||
plugin = static_file
|
||||
plugin_local_path = /tmp/files
|
||||
plugin_strip_prefix = static
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
```
|
||||
|
||||
2. Visit `http://x.x.x.x:6000/static/` from your browser and specify correct username and password to view files in `/tmp/files` on the `frpc` machine.
|
||||
|
||||
### Enable HTTPS for a local HTTP(S) service
|
||||
|
||||
You may substitute `https2https` for the plugin, and point the `plugin_local_addr` to a HTTPS endpoint.
|
||||
|
||||
1. Start `frpc` with the following configuration:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[test_https2http]
|
||||
type = https
|
||||
custom_domains = test.example.com
|
||||
|
||||
plugin = https2http
|
||||
plugin_local_addr = 127.0.0.1:80
|
||||
plugin_crt_path = ./server.crt
|
||||
plugin_key_path = ./server.key
|
||||
plugin_host_header_rewrite = 127.0.0.1
|
||||
plugin_header_X-From-Where = frp
|
||||
```
|
||||
|
||||
2. Visit `https://test.example.com`.
|
||||
|
||||
### Expose your service privately
|
||||
|
||||
To mitigate risks associated with exposing certain services directly to the public network, STCP (Secret TCP) mode requires a preshared key to be used for access to the service from other clients.
|
||||
|
||||
Configure `frps` same as above.
|
||||
|
||||
1. Start `frpc` on machine B with the following config. This example is for exposing the SSH service (port 22), and note the `sk` field for the preshared key, and that the `remote_port` field is removed here:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[secret_ssh]
|
||||
type = stcp
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
```
|
||||
|
||||
2. Start another `frpc` (typically on another machine C) with the following config to access the SSH service with a security key (`sk` field):
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[secret_ssh_visitor]
|
||||
type = stcp
|
||||
role = visitor
|
||||
server_name = secret_ssh
|
||||
sk = abcdefg
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 6000
|
||||
```
|
||||
|
||||
3. On machine C, connect to SSH on machine B, using this command:
|
||||
|
||||
`ssh -oPort=6000 127.0.0.1`
|
||||
|
||||
### P2P Mode
|
||||
|
||||
**xtcp** is designed to transmit large amounts of data directly between clients. A frps server is still needed, as P2P here only refers to the actual data transmission.
|
||||
|
||||
Note that it may not work with all types of NAT devices. You might want to fallback to stcp if xtcp doesn't work.
|
||||
|
||||
1. In `frps.ini` configure a UDP port for xtcp:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
bind_udp_port = 7001
|
||||
```
|
||||
|
||||
2. Start `frpc` on machine B, and expose the SSH port. Note that the `remote_port` field is removed:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[p2p_ssh]
|
||||
type = xtcp
|
||||
sk = abcdefg
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
```
|
||||
|
||||
3. Start another `frpc` (typically on another machine C) with the configuration to connect to SSH using P2P mode:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[p2p_ssh_visitor]
|
||||
type = xtcp
|
||||
role = visitor
|
||||
server_name = p2p_ssh
|
||||
sk = abcdefg
|
||||
bind_addr = 127.0.0.1
|
||||
bind_port = 6000
|
||||
```
|
||||
|
||||
4. On machine C, connect to SSH on machine B, using this command:
|
||||
|
||||
`ssh -oPort=6000 127.0.0.1`
|
||||
|
||||
## Features
|
||||
|
||||
### Configuration Files
|
||||
|
||||
Read the full example configuration files to find out even more features not described here.
|
||||
|
||||
[Full configuration file for frps (Server)](./conf/frps_full.ini)
|
||||
|
||||
[Full configuration file for frpc (Client)](./conf/frpc_full.ini)
|
||||
|
||||
### Using Environment Variables
|
||||
|
||||
Environment variables can be referenced in the configuration file, using Go's standard format:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = {{ .Envs.FRP_SERVER_ADDR }}
|
||||
server_port = 7000
|
||||
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = {{ .Envs.FRP_SSH_REMOTE_PORT }}
|
||||
```
|
||||
|
||||
With the config above, variables can be passed into `frpc` program like this:
|
||||
|
||||
```
|
||||
export FRP_SERVER_ADDR="x.x.x.x"
|
||||
export FRP_SSH_REMOTE_PORT="6000"
|
||||
./frpc -c ./frpc.ini
|
||||
```
|
||||
|
||||
`frpc` will render configuration file template using OS environment variables. Remember to prefix your reference with `.Envs`.
|
||||
|
||||
### Split Configures Into Different Files
|
||||
|
||||
You can split multiple proxy configs into different files and include them in the main file.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
includes=./confd/*.ini
|
||||
```
|
||||
|
||||
```ini
|
||||
# ./confd/test.ini
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
```
|
||||
|
||||
### Dashboard
|
||||
|
||||
Check frp's status and proxies' statistics information by Dashboard.
|
||||
|
||||
Configure a port for dashboard to enable this feature:
|
||||
|
||||
```ini
|
||||
[common]
|
||||
dashboard_port = 7500
|
||||
# dashboard's username and password are both optional
|
||||
dashboard_user = admin
|
||||
dashboard_pwd = admin
|
||||
```
|
||||
|
||||
Then visit `http://[server_addr]:7500` to see the dashboard, with username and password both being `admin`.
|
||||
|
||||
Additionally, you can use HTTPS port by using your domains wildcard or normal SSL certificate:
|
||||
|
||||
```ini
|
||||
[common]
|
||||
dashboard_port = 7500
|
||||
# dashboard's username and password are both optional
|
||||
dashboard_user = admin
|
||||
dashboard_pwd = admin
|
||||
dashboard_tls_mode = true
|
||||
dashboard_tls_cert_file = server.crt
|
||||
dashboard_tls_key_file = server.key
|
||||
```
|
||||
|
||||
Then visit `https://[server_addr]:7500` to see the dashboard in secure HTTPS connection, with username and password both being `admin`.
|
||||
|
||||

|
||||
|
||||
### Admin UI
|
||||
|
||||
The Admin UI helps you check and manage frpc's configuration.
|
||||
|
||||
Configure an address for admin UI to enable this feature:
|
||||
|
||||
```ini
|
||||
[common]
|
||||
admin_addr = 127.0.0.1
|
||||
admin_port = 7400
|
||||
admin_user = admin
|
||||
admin_pwd = admin
|
||||
```
|
||||
|
||||
Then visit `http://127.0.0.1:7400` to see admin UI, with username and password both being `admin`.
|
||||
|
||||
### Monitor
|
||||
|
||||
When dashboard is enabled, frps will save monitor data in cache. It will be cleared after process restart.
|
||||
|
||||
Prometheus is also supported.
|
||||
|
||||
#### Prometheus
|
||||
|
||||
Enable dashboard first, then configure `enable_prometheus = true` in `frps.ini`.
|
||||
|
||||
`http://{dashboard_addr}/metrics` will provide prometheus monitor data.
|
||||
|
||||
### Authenticating the Client
|
||||
|
||||
There are 2 authentication methods to authenticate frpc with frps.
|
||||
|
||||
You can decide which one to use by configuring `authentication_method` under `[common]` in `frpc.ini` and `frps.ini`.
|
||||
|
||||
Configuring `authenticate_heartbeats = true` under `[common]` will use the configured authentication method to add and validate authentication on every heartbeat between frpc and frps.
|
||||
|
||||
Configuring `authenticate_new_work_conns = true` under `[common]` will do the same for every new work connection between frpc and frps.
|
||||
|
||||
#### Token Authentication
|
||||
|
||||
When specifying `authentication_method = token` under `[common]` in `frpc.ini` and `frps.ini` - token based authentication will be used.
|
||||
|
||||
Make sure to specify the same `token` in the `[common]` section in `frps.ini` and `frpc.ini` for frpc to pass frps validation
|
||||
|
||||
#### OIDC Authentication
|
||||
|
||||
When specifying `authentication_method = oidc` under `[common]` in `frpc.ini` and `frps.ini` - OIDC based authentication will be used.
|
||||
|
||||
OIDC stands for OpenID Connect, and the flow used is called [Client Credentials Grant](https://tools.ietf.org/html/rfc6749#section-4.4).
|
||||
|
||||
To use this authentication type - configure `frpc.ini` and `frps.ini` as follows:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
authentication_method = oidc
|
||||
oidc_issuer = https://example-oidc-issuer.com/
|
||||
oidc_audience = https://oidc-audience.com/.default
|
||||
```
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
authentication_method = oidc
|
||||
oidc_client_id = 98692467-37de-409a-9fac-bb2585826f18 # Replace with OIDC client ID
|
||||
oidc_client_secret = oidc_secret
|
||||
oidc_audience = https://oidc-audience.com/.default
|
||||
oidc_token_endpoint_url = https://example-oidc-endpoint.com/oauth2/v2.0/token
|
||||
```
|
||||
|
||||
### Encryption and Compression
|
||||
|
||||
The features are off by default. You can turn on encryption and/or compression:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
use_encryption = true
|
||||
use_compression = true
|
||||
```
|
||||
|
||||
#### TLS
|
||||
|
||||
frp supports the TLS protocol between `frpc` and `frps` since v0.25.0.
|
||||
|
||||
For port multiplexing, frp sends a first byte `0x17` to dial a TLS connection.
|
||||
|
||||
Configure `tls_enable = true` in the `[common]` section to `frpc.ini` to enable this feature.
|
||||
|
||||
To **enforce** `frps` to only accept TLS connections - configure `tls_only = true` in the `[common]` section in `frps.ini`. **This is optional.**
|
||||
|
||||
**`frpc` TLS settings (under the `[common]` section):**
|
||||
```ini
|
||||
tls_enable = true
|
||||
tls_cert_file = certificate.crt
|
||||
tls_key_file = certificate.key
|
||||
tls_trusted_ca_file = ca.crt
|
||||
```
|
||||
|
||||
**`frps` TLS settings (under the `[common]` section):**
|
||||
```ini
|
||||
tls_only = true
|
||||
tls_enable = true
|
||||
tls_cert_file = certificate.crt
|
||||
tls_key_file = certificate.key
|
||||
tls_trusted_ca_file = ca.crt
|
||||
```
|
||||
|
||||
You will need **a root CA cert** and **at least one SSL/TLS certificate**. It **can** be self-signed or regular (such as Let's Encrypt or another SSL/TLS certificate provider).
|
||||
|
||||
If you using `frp` via IP address and not hostname, make sure to set the appropriate IP address in the Subject Alternative Name (SAN) area when generating SSL/TLS Certificates.
|
||||
|
||||
Given an example:
|
||||
|
||||
* Prepare openssl config file. It exists at `/etc/pki/tls/openssl.cnf` in Linux System and `/System/Library/OpenSSL/openssl.cnf` in MacOS, and you can copy it to current path, like `cp /etc/pki/tls/openssl.cnf ./my-openssl.cnf`. If not, you can build it by yourself, like:
|
||||
```
|
||||
cat > my-openssl.cnf << EOF
|
||||
[ ca ]
|
||||
default_ca = CA_default
|
||||
[ CA_default ]
|
||||
x509_extensions = usr_cert
|
||||
[ req ]
|
||||
default_bits = 2048
|
||||
default_md = sha256
|
||||
default_keyfile = privkey.pem
|
||||
distinguished_name = req_distinguished_name
|
||||
attributes = req_attributes
|
||||
x509_extensions = v3_ca
|
||||
string_mask = utf8only
|
||||
[ req_distinguished_name ]
|
||||
[ req_attributes ]
|
||||
[ usr_cert ]
|
||||
basicConstraints = CA:FALSE
|
||||
nsComment = "OpenSSL Generated Certificate"
|
||||
subjectKeyIdentifier = hash
|
||||
authorityKeyIdentifier = keyid,issuer
|
||||
[ v3_ca ]
|
||||
subjectKeyIdentifier = hash
|
||||
authorityKeyIdentifier = keyid:always,issuer
|
||||
basicConstraints = CA:true
|
||||
EOF
|
||||
```
|
||||
|
||||
* build ca certificates:
|
||||
```
|
||||
openssl genrsa -out ca.key 2048
|
||||
openssl req -x509 -new -nodes -key ca.key -subj "/CN=example.ca.com" -days 5000 -out ca.crt
|
||||
```
|
||||
|
||||
* build frps certificates:
|
||||
```
|
||||
openssl genrsa -out server.key 2048
|
||||
|
||||
openssl req -new -sha256 -key server.key \
|
||||
-subj "/C=XX/ST=DEFAULT/L=DEFAULT/O=DEFAULT/CN=server.com" \
|
||||
-reqexts SAN \
|
||||
-config <(cat my-openssl.cnf <(printf "\n[SAN]\nsubjectAltName=DNS:localhost,IP:127.0.0.1,DNS:example.server.com")) \
|
||||
-out server.csr
|
||||
|
||||
openssl x509 -req -days 365 -sha256 \
|
||||
-in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
|
||||
-extfile <(printf "subjectAltName=DNS:localhost,IP:127.0.0.1,DNS:example.server.com") \
|
||||
-out server.crt
|
||||
```
|
||||
|
||||
* build frpc certificates:
|
||||
```
|
||||
openssl genrsa -out client.key 2048
|
||||
openssl req -new -sha256 -key client.key \
|
||||
-subj "/C=XX/ST=DEFAULT/L=DEFAULT/O=DEFAULT/CN=client.com" \
|
||||
-reqexts SAN \
|
||||
-config <(cat my-openssl.cnf <(printf "\n[SAN]\nsubjectAltName=DNS:client.com,DNS:example.client.com")) \
|
||||
-out client.csr
|
||||
|
||||
openssl x509 -req -days 365 -sha256 \
|
||||
-in client.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
|
||||
-extfile <(printf "subjectAltName=DNS:client.com,DNS:example.client.com") \
|
||||
-out client.crt
|
||||
```
|
||||
|
||||
### Hot-Reloading frpc configuration
|
||||
|
||||
The `admin_addr` and `admin_port` fields are required for enabling HTTP API:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
admin_addr = 127.0.0.1
|
||||
admin_port = 7400
|
||||
```
|
||||
|
||||
Then run command `frpc reload -c ./frpc.ini` and wait for about 10 seconds to let `frpc` create or update or remove proxies.
|
||||
|
||||
**Note that parameters in [common] section won't be modified except 'start'.**
|
||||
|
||||
You can run command `frpc verify -c ./frpc.ini` before reloading to check if there are config errors.
|
||||
|
||||
### Get proxy status from client
|
||||
|
||||
Use `frpc status -c ./frpc.ini` to get status of all proxies. The `admin_addr` and `admin_port` fields are required for enabling HTTP API.
|
||||
|
||||
### Only allowing certain ports on the server
|
||||
|
||||
`allow_ports` in `frps.ini` is used to avoid abuse of ports:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
allow_ports = 2000-3000,3001,3003,4000-50000
|
||||
```
|
||||
|
||||
`allow_ports` consists of specific ports or port ranges (lowest port number, dash `-`, highest port number), separated by comma `,`.
|
||||
|
||||
### Port Reuse
|
||||
|
||||
`vhost_http_port` and `vhost_https_port` in frps can use same port with `bind_port`. frps will detect the connection's protocol and handle it correspondingly.
|
||||
|
||||
We would like to try to allow multiple proxies bind a same remote port with different protocols in the future.
|
||||
|
||||
### Bandwidth Limit
|
||||
|
||||
#### For Each Proxy
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[ssh]
|
||||
type = tcp
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
bandwidth_limit = 1MB
|
||||
```
|
||||
|
||||
Set `bandwidth_limit` in each proxy's configure to enable this feature. Supported units are `MB` and `KB`.
|
||||
|
||||
Set `bandwidth_limit_mode` to `client` or `server` to limit bandwidth on the client or server side. Default is `client`.
|
||||
|
||||
### TCP Stream Multiplexing
|
||||
|
||||
frp supports tcp stream multiplexing since v0.10.0 like HTTP2 Multiplexing, in which case all logic connections to the same frpc are multiplexed into the same TCP connection.
|
||||
|
||||
You can disable this feature by modify `frps.ini` and `frpc.ini`:
|
||||
|
||||
```ini
|
||||
# frps.ini and frpc.ini, must be same
|
||||
[common]
|
||||
tcp_mux = false
|
||||
```
|
||||
|
||||
### Support KCP Protocol
|
||||
|
||||
KCP is a fast and reliable protocol that can achieve the transmission effect of a reduction of the average latency by 30% to 40% and reduction of the maximum delay by a factor of three, at the cost of 10% to 20% more bandwidth wasted than TCP.
|
||||
|
||||
KCP mode uses UDP as the underlying transport. Using KCP in frp:
|
||||
|
||||
1. Enable KCP in frps:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
# Specify a UDP port for KCP.
|
||||
kcp_bind_port = 7000
|
||||
```
|
||||
|
||||
The `kcp_bind_port` number can be the same number as `bind_port`, since `bind_port` field specifies a TCP port.
|
||||
|
||||
2. Configure `frpc.ini` to use KCP to connect to frps:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
# Same as the 'kcp_bind_port' in frps.ini
|
||||
server_port = 7000
|
||||
protocol = kcp
|
||||
```
|
||||
|
||||
### Support QUIC Protocol
|
||||
|
||||
QUIC is a new multiplexed transport built on top of UDP.
|
||||
|
||||
Using QUIC in frp:
|
||||
|
||||
1. Enable QUIC in frps:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
# Specify a UDP port for QUIC.
|
||||
quic_bind_port = 7000
|
||||
```
|
||||
|
||||
The `quic_bind_port` number can be the same number as `bind_port`, since `bind_port` field specifies a TCP port.
|
||||
|
||||
2. Configure `frpc.ini` to use QUIC to connect to frps:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
# Same as the 'quic_bind_port' in frps.ini
|
||||
server_port = 7000
|
||||
protocol = quic
|
||||
```
|
||||
|
||||
### Connection Pooling
|
||||
|
||||
By default, frps creates a new frpc connection to the backend service upon a user request. With connection pooling, frps keeps a certain number of pre-established connections, reducing the time needed to establish a connection.
|
||||
|
||||
This feature is suitable for a large number of short connections.
|
||||
|
||||
1. Configure the limit of pool count each proxy can use in `frps.ini`:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
max_pool_count = 5
|
||||
```
|
||||
|
||||
2. Enable and specify the number of connection pool:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
pool_count = 1
|
||||
```
|
||||
|
||||
### Load balancing
|
||||
|
||||
Load balancing is supported by `group`.
|
||||
|
||||
This feature is only available for types `tcp`, `http`, `tcpmux` now.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[test1]
|
||||
type = tcp
|
||||
local_port = 8080
|
||||
remote_port = 80
|
||||
group = web
|
||||
group_key = 123
|
||||
|
||||
[test2]
|
||||
type = tcp
|
||||
local_port = 8081
|
||||
remote_port = 80
|
||||
group = web
|
||||
group_key = 123
|
||||
```
|
||||
|
||||
`group_key` is used for authentication.
|
||||
|
||||
Connections to port 80 will be dispatched to proxies in the same group randomly.
|
||||
|
||||
For type `tcp`, `remote_port` in the same group should be the same.
|
||||
|
||||
For type `http`, `custom_domains`, `subdomain`, `locations` should be the same.
|
||||
|
||||
### Service Health Check
|
||||
|
||||
Health check feature can help you achieve high availability with load balancing.
|
||||
|
||||
Add `health_check_type = tcp` or `health_check_type = http` to enable health check.
|
||||
|
||||
With health check type **tcp**, the service port will be pinged (TCPing):
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[test1]
|
||||
type = tcp
|
||||
local_port = 22
|
||||
remote_port = 6000
|
||||
# Enable TCP health check
|
||||
health_check_type = tcp
|
||||
# TCPing timeout seconds
|
||||
health_check_timeout_s = 3
|
||||
# If health check failed 3 times in a row, the proxy will be removed from frps
|
||||
health_check_max_failed = 3
|
||||
# A health check every 10 seconds
|
||||
health_check_interval_s = 10
|
||||
```
|
||||
|
||||
With health check type **http**, an HTTP request will be sent to the service and an HTTP 2xx OK response is expected:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
# Enable HTTP health check
|
||||
health_check_type = http
|
||||
# frpc will send a GET request to '/status'
|
||||
# and expect an HTTP 2xx OK response
|
||||
health_check_url = /status
|
||||
health_check_timeout_s = 3
|
||||
health_check_max_failed = 3
|
||||
health_check_interval_s = 10
|
||||
```
|
||||
|
||||
### Rewriting the HTTP Host Header
|
||||
|
||||
By default frp does not modify the tunneled HTTP requests at all as it's a byte-for-byte copy.
|
||||
|
||||
However, speaking of web servers and HTTP requests, your web server might rely on the `Host` HTTP header to determine the website to be accessed. frp can rewrite the `Host` header when forwarding the HTTP requests, with the `host_header_rewrite` field:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
host_header_rewrite = dev.example.com
|
||||
```
|
||||
|
||||
The HTTP request will have the `Host` header rewritten to `Host: dev.example.com` when it reaches the actual web server, although the request from the browser probably has `Host: test.example.com`.
|
||||
|
||||
### Setting other HTTP Headers
|
||||
|
||||
Similar to `Host`, You can override other HTTP request headers with proxy type `http`.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
host_header_rewrite = dev.example.com
|
||||
header_X-From-Where = frp
|
||||
```
|
||||
|
||||
Note that parameter(s) prefixed with `header_` will be added to HTTP request headers.
|
||||
|
||||
In this example, it will set header `X-From-Where: frp` in the HTTP request.
|
||||
|
||||
### Get Real IP
|
||||
|
||||
#### HTTP X-Forwarded-For
|
||||
|
||||
This feature is for http proxy only.
|
||||
|
||||
You can get user's real IP from HTTP request headers `X-Forwarded-For`.
|
||||
|
||||
#### Proxy Protocol
|
||||
|
||||
frp supports Proxy Protocol to send user's real IP to local services. It support all types except UDP.
|
||||
|
||||
Here is an example for https service:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = https
|
||||
local_port = 443
|
||||
custom_domains = test.example.com
|
||||
|
||||
# now v1 and v2 are supported
|
||||
proxy_protocol_version = v2
|
||||
```
|
||||
|
||||
You can enable Proxy Protocol support in nginx to expose user's real IP in HTTP header `X-Real-IP`, and then read `X-Real-IP` header in your web service for the real IP.
|
||||
|
||||
### Require HTTP Basic Auth (Password) for Web Services
|
||||
|
||||
Anyone who can guess your tunnel URL can access your local web server unless you protect it with a password.
|
||||
|
||||
This enforces HTTP Basic Auth on all requests with the username and password specified in frpc's configure file.
|
||||
|
||||
It can only be enabled when proxy type is http.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = test.example.com
|
||||
http_user = abc
|
||||
http_pwd = abc
|
||||
```
|
||||
|
||||
Visit `http://test.example.com` in the browser and now you are prompted to enter the username and password.
|
||||
|
||||
### Custom Subdomain Names
|
||||
|
||||
It is convenient to use `subdomain` configure for http and https types when many people share one frps server.
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
subdomain_host = frps.com
|
||||
```
|
||||
|
||||
Resolve `*.frps.com` to the frps server's IP. This is usually called a Wildcard DNS record.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web]
|
||||
type = http
|
||||
local_port = 80
|
||||
subdomain = test
|
||||
```
|
||||
|
||||
Now you can visit your web service on `test.frps.com`.
|
||||
|
||||
Note that if `subdomain_host` is not empty, `custom_domains` should not be the subdomain of `subdomain_host`.
|
||||
|
||||
### URL Routing
|
||||
|
||||
frp supports forwarding HTTP requests to different backend web services by url routing.
|
||||
|
||||
`locations` specifies the prefix of URL used for routing. frps first searches for the most specific prefix location given by literal strings regardless of the listed order.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[web01]
|
||||
type = http
|
||||
local_port = 80
|
||||
custom_domains = web.example.com
|
||||
locations = /
|
||||
|
||||
[web02]
|
||||
type = http
|
||||
local_port = 81
|
||||
custom_domains = web.example.com
|
||||
locations = /news,/about
|
||||
```
|
||||
|
||||
HTTP requests with URL prefix `/news` or `/about` will be forwarded to **web02** and other requests to **web01**.
|
||||
|
||||
### TCP Port Multiplexing
|
||||
|
||||
frp supports receiving TCP sockets directed to different proxies on a single port on frps, similar to `vhost_http_port` and `vhost_https_port`.
|
||||
|
||||
The only supported TCP port multiplexing method available at the moment is `httpconnect` - HTTP CONNECT tunnel.
|
||||
|
||||
When setting `tcpmux_httpconnect_port` to anything other than 0 in frps under `[common]`, frps will listen on this port for HTTP CONNECT requests.
|
||||
|
||||
The host of the HTTP CONNECT request will be used to match the proxy in frps. Proxy hosts can be configured in frpc by configuring `custom_domain` and / or `subdomain` under `type = tcpmux` proxies, when `multiplexer = httpconnect`.
|
||||
|
||||
For example:
|
||||
|
||||
```ini
|
||||
# frps.ini
|
||||
[common]
|
||||
bind_port = 7000
|
||||
tcpmux_httpconnect_port = 1337
|
||||
```
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
|
||||
[proxy1]
|
||||
type = tcpmux
|
||||
multiplexer = httpconnect
|
||||
custom_domains = test1
|
||||
local_port = 80
|
||||
|
||||
[proxy2]
|
||||
type = tcpmux
|
||||
multiplexer = httpconnect
|
||||
custom_domains = test2
|
||||
local_port = 8080
|
||||
```
|
||||
|
||||
In the above configuration - frps can be contacted on port 1337 with a HTTP CONNECT header such as:
|
||||
|
||||
```
|
||||
CONNECT test1 HTTP/1.1\r\n\r\n
|
||||
```
|
||||
and the connection will be routed to `proxy1`.
|
||||
|
||||
### Connecting to frps via HTTP PROXY
|
||||
|
||||
frpc can connect to frps using HTTP proxy if you set OS environment variable `HTTP_PROXY`, or if `http_proxy` is set in frpc.ini file.
|
||||
|
||||
It only works when protocol is tcp.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[common]
|
||||
server_addr = x.x.x.x
|
||||
server_port = 7000
|
||||
http_proxy = http://user:pwd@192.168.1.128:8080
|
||||
```
|
||||
|
||||
### Range ports mapping
|
||||
|
||||
Proxy with names that start with `range:` will support mapping range ports.
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[range:test_tcp]
|
||||
type = tcp
|
||||
local_ip = 127.0.0.1
|
||||
local_port = 6000-6006,6007
|
||||
remote_port = 6000-6006,6007
|
||||
```
|
||||
|
||||
frpc will generate 8 proxies like `test_tcp_0`, `test_tcp_1`, ..., `test_tcp_7`.
|
||||
|
||||
### Client Plugins
|
||||
|
||||
frpc only forwards requests to local TCP or UDP ports by default.
|
||||
|
||||
Plugins are used for providing rich features. There are built-in plugins such as `unix_domain_socket`, `http_proxy`, `socks5`, `static_file`, `http2https`, `https2http`, `https2https` and you can see [example usage](#example-usage).
|
||||
|
||||
Specify which plugin to use with the `plugin` parameter. Configuration parameters of plugin should be started with `plugin_`. `local_ip` and `local_port` are not used for plugin.
|
||||
|
||||
Using plugin **http_proxy**:
|
||||
|
||||
```ini
|
||||
# frpc.ini
|
||||
[http_proxy]
|
||||
type = tcp
|
||||
remote_port = 6000
|
||||
plugin = http_proxy
|
||||
plugin_http_user = abc
|
||||
plugin_http_passwd = abc
|
||||
```
|
||||
|
||||
`plugin_http_user` and `plugin_http_passwd` are configuration parameters used in `http_proxy` plugin.
|
||||
|
||||
### Server Manage Plugins
|
||||
|
||||
Read the [document](/doc/server_plugin.md).
|
||||
|
||||
Find more plugins in [gofrp/plugin](https://github.com/gofrp/plugin).
|
||||
|
||||
## Development Plan
|
||||
|
||||
* Log HTTP request information in frps.
|
||||
|
||||
## Contributing
|
||||
|
||||
Interested in getting involved? We would like to help you!
|
||||
|
||||
* Take a look at our [issues list](https://github.com/fatedier/frp/issues) and consider sending a Pull Request to **dev branch**.
|
||||
* If you want to add a new feature, please create an issue first to describe the new feature, as well as the implementation approach. Once a proposal is accepted, create an implementation of the new features and submit it as a pull request.
|
||||
* Sorry for my poor English. Improvements for this document are welcome, even some typo fixes.
|
||||
* If you have great ideas, send an email to fatedier@gmail.com.
|
||||
|
||||
**Note: We prefer you to give your advise in [issues](https://github.com/fatedier/frp/issues), so others with a same question can search it quickly and we don't need to answer them repeatedly.**
|
||||
|
||||
## Donation
|
||||
|
||||
If frp helps you a lot, you can support us by:
|
||||
|
||||
### GitHub Sponsors
|
||||
|
||||
Support us by [Github Sponsors](https://github.com/sponsors/fatedier).
|
||||
|
||||
You can have your company's logo placed on README file of this project.
|
||||
|
||||
### PayPal
|
||||
|
||||
Donate money by [PayPal](https://www.paypal.me/fatedier) to my account **fatedier@gmail.com**.
|
||||
|
||||
20
apps/frps/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: frps-frp服务端
|
||||
tags:
|
||||
- 工具
|
||||
title: frp是一种反向代理工具,常用于内网穿透(服务端)
|
||||
type: 工具
|
||||
description: frp是一种反向代理工具,常用于内网穿透(服务端)
|
||||
additionalProperties:
|
||||
key: frps
|
||||
name: frps-frp服务端
|
||||
tags:
|
||||
- Tool
|
||||
shortDescZh: frp是一种反向代理工具,常用于内网穿透(服务端)
|
||||
shortDescEn: frp is a reverse proxy tool that is commonly used for intranet penetration(Server)
|
||||
type: tool
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://github.com/fatedier/frp
|
||||
github: https://github.com/fatedier/frp
|
||||
document: https://github.com/fatedier/frp/blob/dev/README_zh.md
|
||||
BIN
apps/frps/logo.png
Normal file
|
After Width: | Height: | Size: 26 KiB |
102
apps/hexo/README.md
Normal file
@ -0,0 +1,102 @@
|
||||
<img src="https://raw.githubusercontent.com/hexojs/logo/master/hexo-logo-avatar.png" alt="Hexo logo" width="100" height="100" align="right" />
|
||||
|
||||
# Hexo
|
||||
|
||||
> A fast, simple & powerful blog framework, powered by [Node.js](https://nodejs.org).
|
||||
|
||||
[Website](https://hexo.io) |
|
||||
[Documentation](https://hexo.io/docs/) |
|
||||
[Installation Guide](https://hexo.io/docs/#Installation) |
|
||||
[Contribution Guide](https://hexo.io/docs/contributing) |
|
||||
[Code of Conduct](CODE_OF_CONDUCT.md) |
|
||||
[API](https://hexo.io/api/) |
|
||||
[Twitter](https://twitter.com/hexojs)
|
||||
|
||||
[](https://www.npmjs.com/package/hexo)
|
||||

|
||||
[](https://github.com/hexojs/hexo/actions?query=workflow%3ATester)
|
||||
[](https://libraries.io/npm/hexo)
|
||||
[](https://coveralls.io/r/hexojs/hexo?branch=master)
|
||||
[](https://gitter.im/hexojs/hexo)
|
||||
[](https://discord.gg/teM2Anj)
|
||||
[](https://t.me/hexojs)
|
||||
[](https://app.fossa.com/projects/git%2Bgithub.com%2Fhexojs%2Fhexo?ref=badge_shield)
|
||||
[](CODE_OF_CONDUCT.md)
|
||||
|
||||
## Features
|
||||
|
||||
- Blazing fast generating
|
||||
- Support for GitHub Flavored Markdown and most Octopress plugins
|
||||
- One-command deploy to GitHub Pages, Heroku, etc.
|
||||
- Powerful API for limitless extensibility
|
||||
- Hundreds of [themes](https://hexo.io/themes/) & [plugins](https://hexo.io/plugins/)
|
||||
|
||||
## Quick Start
|
||||
|
||||
**Install Hexo**
|
||||
|
||||
``` bash
|
||||
$ npm install hexo-cli -g
|
||||
```
|
||||
|
||||
Install with [brew](https://brew.sh/) on macOS and Linux:
|
||||
|
||||
```bash
|
||||
$ brew install hexo
|
||||
```
|
||||
|
||||
**Setup your blog**
|
||||
|
||||
``` bash
|
||||
$ hexo init blog
|
||||
$ cd blog
|
||||
```
|
||||
|
||||
**Start the server**
|
||||
|
||||
``` bash
|
||||
$ hexo server
|
||||
```
|
||||
|
||||
**Create a new post**
|
||||
|
||||
``` bash
|
||||
$ hexo new "Hello Hexo"
|
||||
```
|
||||
|
||||
**Generate static files**
|
||||
|
||||
``` bash
|
||||
$ hexo generate
|
||||
```
|
||||
|
||||
## More Information
|
||||
|
||||
- Read the [documentation](https://hexo.io/)
|
||||
- Visit the [Awesome Hexo](https://github.com/hexojs/awesome-hexo) list
|
||||
- Find solutions in [troubleshooting](https://hexo.io/docs/troubleshooting.html)
|
||||
- Join discussion on [Google Group](https://groups.google.com/group/hexo), [Discord](https://discord.gg/teM2Anj), [Gitter](https://gitter.im/hexojs/hexo) or [Telegram](https://t.me/hexojs)
|
||||
- See the [plugin list](https://hexo.io/plugins/) and the [theme list](https://hexo.io/themes/) on wiki
|
||||
- Follow [@hexojs](https://twitter.com/hexojs) for latest news
|
||||
|
||||
## Contributing
|
||||
|
||||
We welcome you to join the development of Hexo. Please see [contributing document](https://hexo.io/docs/contributing). 🤗
|
||||
|
||||
Also, we welcome PR or issue to [official-plugins](https://github.com/hexojs).
|
||||
|
||||
## Contributors
|
||||
|
||||
[](https://github.com/hexojs/hexo/graphs/contributors)
|
||||
|
||||
## Backers
|
||||
|
||||
[](https://opencollective.com/hexo)
|
||||
|
||||
## Sponsors
|
||||
|
||||
<a href="https://linktr.ee/rss3"><img src="https://d1fdloi71mui9q.cloudfront.net/8xxahBqRTnecXgXKObeo_L8ks2KjC31fmM5Nd" alt="RSS3" width="200"/></a>
|
||||
|
||||
## License
|
||||
|
||||
[](https://app.fossa.com/projects/git%2Bgithub.com%2Fhexojs%2Fhexo?ref=badge_large)
|
||||
20
apps/hexo/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: Hexo
|
||||
tags:
|
||||
- 建站
|
||||
title: 快速、简洁且高效的博客框架
|
||||
type: 建站
|
||||
description: 快速、简洁且高效的博客框架
|
||||
additionalProperties:
|
||||
key: hexo
|
||||
name: Hexo
|
||||
tags:
|
||||
- WebSite
|
||||
shortDescZh: 快速、简洁且高效的博客框架
|
||||
shortDescEn: A fast, simple & powerful blog framework
|
||||
type: website
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://hexo.io/
|
||||
github: https://github.com/hexojs/hexo
|
||||
document: https://hexo.io/docs/
|
||||
BIN
apps/hexo/logo.png
Normal file
|
After Width: | Height: | Size: 5.2 KiB |
24
apps/hexo/stable-23-07-01/data.yml
Normal file
@ -0,0 +1,24 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: 40064
|
||||
edit: true
|
||||
envKey: PANEL_APP_PORT_HTTP
|
||||
labelEn: Port
|
||||
labelZh: 端口
|
||||
required: true
|
||||
rule: paramPort
|
||||
type: number
|
||||
- default: ""
|
||||
edit: true
|
||||
envKey: GIT_USERNAME
|
||||
labelEn: Git username
|
||||
labelZh: Git 用户名
|
||||
required: true
|
||||
type: text
|
||||
- default: ""
|
||||
edit: true
|
||||
envKey: GIT_MAIL
|
||||
labelEn: Git Email
|
||||
labelZh: Git 邮箱
|
||||
required: true
|
||||
type: text
|
||||
24
apps/hexo/stable-23-07-01/docker-compose.yml
Normal file
@ -0,0 +1,24 @@
|
||||
version: '3'
|
||||
services:
|
||||
hexo:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
networks:
|
||||
- 1panel-network
|
||||
ports:
|
||||
- "${PANEL_APP_PORT_HTTP}:4000"
|
||||
volumes:
|
||||
- "./data:/app"
|
||||
environment:
|
||||
- PUID=1000
|
||||
- PGID=1000
|
||||
- TZ=Asia/Shanghai
|
||||
- GIT_USER=${GIT_USERNAME}
|
||||
- GIT_EMAIL=${GIT_MAIL}
|
||||
image: bloodstar/hexo:stable-23-07-01
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
|
||||
networks:
|
||||
1panel-network:
|
||||
external: true
|
||||
10
apps/home-assistant/2023.8.0.dev20230723/data.yml
Normal file
@ -0,0 +1,10 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: ./data
|
||||
edit: false
|
||||
envKey: DATA_PATH
|
||||
labelEn: Data folder path
|
||||
labelZh: 数据文件夹路径
|
||||
required: true
|
||||
type: text
|
||||
|
||||
13
apps/home-assistant/2023.8.0.dev20230723/docker-compose.yml
Normal file
@ -0,0 +1,13 @@
|
||||
version: '3'
|
||||
services:
|
||||
homeassistant:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
network_mode: "host"
|
||||
volumes:
|
||||
- "${DATA_PATH}:/config"
|
||||
environment:
|
||||
- TZ=Asia/Shanghai
|
||||
image: homeassistant/home-assistant:2023.8.0.dev20230723
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
33
apps/home-assistant/README.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 使用说明
|
||||
|
||||
- 默认访问地址
|
||||
```
|
||||
IP:8123
|
||||
```
|
||||
|
||||
# 原始相关
|
||||
|
||||
# Home Assistant [](https://www.home-assistant.io/join-chat/)
|
||||
|
||||
Open source home automation that puts local control and privacy first.
|
||||
Powered by a worldwide community of tinkerers and DIY enthusiasts.
|
||||
Perfect to run on a Raspberry Pi or a local server.
|
||||
|
||||
Check out [home-assistant.io](https://home-assistant.io) for [ademo](https://demo.home-assistant.io), [installation instructions](https://home-assistant.io/getting-started/),[tutorials](https://home-assistant.io/getting-started/automation/) and [documentation](https://home-assistant.io/docs/).
|
||||
|
||||
[](https://demo.home-assistant.io)
|
||||
|
||||
## Featured integrations
|
||||
|
||||
[](https://home-assistant.io/integrations/)
|
||||
|
||||
The system is built using a modular approach so support for other
|
||||
devices or actions can be implemented easily. See also the [section on
|
||||
architecture](https://developers.home-assistant.io/docs/architecture_index/)
|
||||
and the [section on creating your own
|
||||
components](https://developers.home-assistant.io/docs/creating_component_index/).
|
||||
|
||||
If you run into issues while using Home Assistant or during development
|
||||
of a component, check the [Home Assistant help
|
||||
section](https://home-assistant.io/help/) of our website for further
|
||||
help and information.
|
||||
20
apps/home-assistant/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: Home Assistant
|
||||
tags:
|
||||
- 工具
|
||||
title: 开源家庭自动化,将本地控制和隐私放在首位。
|
||||
type: 工具
|
||||
description: 开源家庭自动化,将本地控制和隐私放在首位。
|
||||
additionalProperties:
|
||||
key: home-assistant
|
||||
name: Home Assistant
|
||||
tags:
|
||||
- Tool
|
||||
shortDescZh: 开源家庭自动化,将本地控制和隐私放在首位。
|
||||
shortDescEn: Open source home automation that puts local control and privacy first.
|
||||
type: tool
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://www.home-assistant.io/
|
||||
github: https://github.com/home-assistant/core
|
||||
document: https://www.home-assistant.io/docs/
|
||||
BIN
apps/home-assistant/logo.png
Normal file
|
After Width: | Height: | Size: 6.9 KiB |
12
apps/nextcloud/27.0.1/data.yml
Normal file
@ -0,0 +1,12 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: 40069
|
||||
edit: true
|
||||
envKey: PANEL_APP_PORT_HTTPS
|
||||
labelEn: HTTPS Port
|
||||
labelZh: HTTPS端口
|
||||
required: true
|
||||
rule: paramPort
|
||||
type: number
|
||||
|
||||
|
||||
23
apps/nextcloud/27.0.1/docker-compose.yml
Normal file
@ -0,0 +1,23 @@
|
||||
version: '3'
|
||||
services:
|
||||
nextcloud:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
networks:
|
||||
- 1panel-network
|
||||
ports:
|
||||
- "${PANEL_APP_PORT_HTTPS}:443"
|
||||
volumes:
|
||||
- "./data/config:/config"
|
||||
- "./data/data:/data"
|
||||
environment:
|
||||
- PUID=1000
|
||||
- PGID=1000
|
||||
- TZ=Asia/Shanghai
|
||||
image: linuxserver/nextcloud:27.0.1
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
|
||||
networks:
|
||||
1panel-network:
|
||||
external: true
|
||||
163
apps/nextcloud/README.md
Normal file
@ -0,0 +1,163 @@
|
||||
# Nextcloud Server ☁
|
||||
[](https://scrutinizer-ci.com/g/nextcloud/server/?branch=master)
|
||||
[](https://codecov.io/gh/nextcloud/server)
|
||||
[](https://bestpractices.coreinfrastructure.org/projects/209)
|
||||
[](https://contribute.design/nextcloud/server)
|
||||
|
||||
**A safe home for all your data.**
|
||||
|
||||
|
||||
|
||||
## Why is this so awesome? 🤩
|
||||
|
||||
* 📁 **Access your Data** You can store your files, contacts, calendars, and more on a server of your choosing.
|
||||
* 🔄 **Sync your Data** You keep your files, contacts, calendars, and more synchronized amongst your devices.
|
||||
* 🙌 **Share your Data** …by giving others access to the stuff you want them to see or to collaborate with.
|
||||
* 🚀 **Expandable with hundreds of Apps** ...like [Calendar](https://github.com/nextcloud/calendar), [Contacts](https://github.com/nextcloud/contacts), [Mail](https://github.com/nextcloud/mail), [Video Chat](https://github.com/nextcloud/spreed) and all those you can discover in our [App Store](https://apps.nextcloud.com)
|
||||
* 🔒 **Security** with our encryption mechanisms, [HackerOne bounty program](https://hackerone.com/nextcloud) and two-factor authentication.
|
||||
|
||||
Do you want to learn more about how you can use Nextcloud to access, share and protect your files, calendars, contacts, communication & more at home and in your organization? [**Learn about all our Features**](https://nextcloud.com/athome/).
|
||||
|
||||
## Get your Nextcloud 🚚
|
||||
|
||||
- ☑️ [**Simply sign up**](https://nextcloud.com/signup/) at one of our providers either through our website or through the apps directly.
|
||||
- 🖥 [**Install** a server by yourself](https://nextcloud.com/install/#instructions-server) on your hardware or by using one of our ready to use **appliances**
|
||||
- 📦 Buy one of the [awesome **devices** coming with a preinstalled Nextcloud](https://nextcloud.com/devices/)
|
||||
- 🏢 Find a [service **provider**](https://nextcloud.com/providers/) who hosts Nextcloud for you or your company
|
||||
|
||||
Enterprise? Public Sector or Education user? You may want to have a look into [**Nextcloud Enterprise**](https://nextcloud.com/enterprise/) provided by Nextcloud GmbH.
|
||||
|
||||
## Get in touch 💬
|
||||
|
||||
* [📋 Forum](https://help.nextcloud.com)
|
||||
* [👥 Facebook](https://www.facebook.com/nextclouders)
|
||||
* [🐣 Twitter](https://twitter.com/Nextclouders)
|
||||
* [🐘 Mastodon](https://mastodon.xyz/@nextcloud)
|
||||
|
||||
You can also [get support for Nextcloud](https://nextcloud.com/support)!
|
||||
|
||||
|
||||
## Join the team 👪
|
||||
|
||||
There are many ways to contribute, of which development is only one! Find out [how to get involved](https://nextcloud.com/contribute/), including as a translator, designer, tester, helping others, and much more! 😍
|
||||
|
||||
|
||||
### Development setup 👩💻
|
||||
|
||||
1. 🚀 [Set up your local development environment](https://docs.nextcloud.com/server/latest/developer_manual/getting_started/devenv.html)
|
||||
2. 🐛 [Pick a good first issue](https://github.com/nextcloud/server/labels/good%20first%20issue)
|
||||
3. 👩🔧 Create a branch and make your changes. Remember to sign off your commits using `git commit -sm "Your commit message"`
|
||||
4. ⬆ Create a [pull request](https://opensource.guide/how-to-contribute/#opening-a-pull-request) and `@mention` the people from the issue to review
|
||||
5. 👍 Fix things that come up during a review
|
||||
6. 🎉 Wait for it to get merged!
|
||||
|
||||
Third-party components are handled as git submodules which have to be initialized first. So aside from the regular git checkout invoking `git submodule update --init` or a similar command is needed, for details see Git documentation.
|
||||
|
||||
Several apps that are included by default in regular releases such as [First run wizard](https://github.com/nextcloud/firstrunwizard) or [Activity](https://github.com/nextcloud/activity) are missing in `master` and have to be installed manually by cloning them into the `apps` subfolder.
|
||||
|
||||
Otherwise, git checkouts can be handled the same as release archives, by using the `stable*` branches. Note they should never be used on production systems.
|
||||
|
||||
### Working with front-end code 🏗
|
||||
|
||||
#### Building Vue components and scripts
|
||||
|
||||
We are moving more and more toward using Vue.js in the front-end, starting with Settings. For building the code on changes, use these terminal commands in the root folder:
|
||||
|
||||
```bash
|
||||
# install dependencies
|
||||
make dev-setup
|
||||
|
||||
# build for development
|
||||
make build-js
|
||||
|
||||
# build for development and watch edits
|
||||
make watch-js
|
||||
|
||||
# build for production with minification
|
||||
make build-js-production
|
||||
```
|
||||
|
||||
#### Building styles
|
||||
|
||||
Styles are written in SCSS and compiled to css.
|
||||
|
||||
```bash
|
||||
# install dependencies
|
||||
make dev-setup
|
||||
|
||||
# compile style sheets
|
||||
npm run sass
|
||||
|
||||
# compile style sheets and watch edits
|
||||
npm run sass:watch
|
||||
```
|
||||
|
||||
#### Committing changes
|
||||
|
||||
**When making changes, also commit the compiled files!**
|
||||
|
||||
We still use Handlebars templates in some places in Files and Settings. We will replace these step-by-step with Vue.js, but in the meantime, you need to compile them separately.
|
||||
|
||||
If you don’t have Handlebars installed yet, you can do it with this terminal command:
|
||||
```bash
|
||||
sudo npm install -g handlebars
|
||||
```
|
||||
|
||||
Then inside the root folder of your local Nextcloud development installation, run this command in the terminal every time you changed a `.handlebars` file to compile it:
|
||||
```bash
|
||||
./build/compile-handlebars-templates.sh
|
||||
```
|
||||
|
||||
Before checking in JS changes, make sure to also build for production:
|
||||
```bash
|
||||
make build-js-production
|
||||
```
|
||||
Then add the compiled files for committing.
|
||||
|
||||
To save some time, to only rebuild for a specific app, use the following and replace the module with the app name:
|
||||
```bash
|
||||
MODULE=user_status make build-js-production
|
||||
```
|
||||
|
||||
Please note that if you used `make build-js` or `make watch-js` before, you'll notice that a lot of files were marked as changed, so might need to clear the workspace first.
|
||||
|
||||
### Working with back-end code 🏗
|
||||
|
||||
When changing back-end PHP code, in general, no additional steps are needed before checking in.
|
||||
|
||||
However, if new files were created, you will need to run the following command to update the autoloader files:
|
||||
```bash
|
||||
build/autoloaderchecker.sh
|
||||
```
|
||||
|
||||
After that, please also include the autoloader file changes in your commits.
|
||||
|
||||
### Tools we use 🛠
|
||||
|
||||
- [👀 BrowserStack](https://browserstack.com) for cross-browser testing
|
||||
- [🌊 WAVE](https://wave.webaim.org/extension/) for accessibility testing
|
||||
- [🚨 Lighthouse](https://developers.google.com/web/tools/lighthouse/) for testing performance, accessibility, and more
|
||||
|
||||
#### Helpful bots at github :robot:
|
||||
|
||||
- Comment on a pull request with `/update-3rdparty` to update the 3rd party submodule. It will update to the last commit of the 3rd party branch named like the PR target.
|
||||
|
||||
## Contribution guidelines 📜
|
||||
|
||||
All contributions to this repository from June 16, 2016, and onward are considered to be
|
||||
licensed under the AGPLv3 or any later version.
|
||||
|
||||
Nextcloud doesn't require a CLA (Contributor License Agreement).
|
||||
The copyright belongs to all the individual contributors. Therefore we recommend
|
||||
that every contributor adds the following line to the header of a file if they
|
||||
changed it substantially:
|
||||
|
||||
```
|
||||
@copyright Copyright (c) <year>, <your name> (<your email address>)
|
||||
```
|
||||
|
||||
Please read the [Code of Conduct](https://nextcloud.com/community/code-of-conduct/). This document offers some guidance to ensure Nextcloud participants can cooperate effectively in a positive and inspiring atmosphere, and to explain how together we can strengthen and support each other.
|
||||
|
||||
Please review the [guidelines for contributing](.github/CONTRIBUTING.md) to this repository.
|
||||
|
||||
More information how to contribute: [https://nextcloud.com/contribute/](https://nextcloud.com/contribute/)
|
||||
20
apps/nextcloud/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: Nextcloud
|
||||
tags:
|
||||
- 建站
|
||||
title: Nextcloud服务器,所有数据的安全家园
|
||||
type: 建站
|
||||
description: Nextcloud服务器,所有数据的安全家园
|
||||
additionalProperties:
|
||||
key: nextcloud
|
||||
name: Nextcloud
|
||||
tags:
|
||||
- WebSite
|
||||
shortDescZh: Nextcloud服务器,所有数据的安全家园
|
||||
shortDescEn: Nextcloud server, a safe home for all your data
|
||||
type: website
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://nextcloud.com/
|
||||
github: https://github.com/nextcloud/server
|
||||
document: https://docs.nextcloud.com/
|
||||
BIN
apps/nextcloud/logo.png
Normal file
|
After Width: | Height: | Size: 8.8 KiB |
17
apps/zfile/4.1.5/data.yml
Normal file
@ -0,0 +1,17 @@
|
||||
additionalProperties:
|
||||
formFields:
|
||||
- default: 40072
|
||||
edit: true
|
||||
envKey: PANEL_APP_PORT_HTTP
|
||||
labelEn: Port
|
||||
labelZh: 端口
|
||||
required: true
|
||||
rule: paramPort
|
||||
type: number
|
||||
- default: ./data/mnt
|
||||
edit: true
|
||||
envKey: MOUNT_PATH
|
||||
labelEn: Mount folder path
|
||||
labelZh: 挂载文件夹路径
|
||||
required: true
|
||||
type: text
|
||||
20
apps/zfile/4.1.5/docker-compose.yml
Normal file
@ -0,0 +1,20 @@
|
||||
version: '3'
|
||||
services:
|
||||
zfile:
|
||||
container_name: ${CONTAINER_NAME}
|
||||
restart: always
|
||||
networks:
|
||||
- 1panel-network
|
||||
ports:
|
||||
- "${PANEL_APP_PORT_HTTP}:8080"
|
||||
volumes:
|
||||
- "./data/db:/root/.zfile-v4/db"
|
||||
- "./data/logs:/root/.zfile-v4/logs"
|
||||
- "${MOUNT_PATH}:/data/file"
|
||||
image: zhaojun1998/zfile:4.1.5
|
||||
labels:
|
||||
createdBy: "Apps"
|
||||
|
||||
networks:
|
||||
1panel-network:
|
||||
external: true
|
||||
71
apps/zfile/README.md
Normal file
@ -0,0 +1,71 @@
|
||||
# ZFile
|
||||
|
||||
[](https://github.com/zfile-dev/zfile/blob/main/LICENSE)
|
||||
[](https://github.com/zfile-dev/zfile/releases)
|
||||
<img src="https://api.codacy.com/project/badge/Grade/70b793267f7941d58cbd93f50c9a8e0a"/>
|
||||
|
||||
|
||||
## ZFile 是什么?
|
||||
|
||||
ZFile 是一个适用于个人的在线网盘(列目录)程序,可以将你各个存储类型的存储源,统一到一个网页中查看、预览、维护,再也不用去登录各种各样的网页登录后管理文件,现在你只需要在 ZFile 中使用。你只需要填写存储源相关信息,其他的令牌刷新,授权都是尽量自动化的,且有完善的文档帮助你使用。
|
||||
|
||||
- 支持对接 S3、OneDrive、SharePoint、Google Drive、多吉云、又拍云、本地存储、FTP、SFTP 等存储源
|
||||
- 支持在线浏览图片、播放音视频,文本文件、Office、obj(3d)等文件类型。
|
||||
|
||||
## 快速开始
|
||||
|
||||
请参考部署文档: [https://docs.zfile.vip](https://docs.zfile.vip)
|
||||
|
||||
## 在线体验
|
||||
|
||||
[https://demo.zfile.vip](https://demo.zfile.vip)
|
||||
|
||||
## 功能预览
|
||||
|
||||
### 文件列表
|
||||
|
||||
### 画廊模式
|
||||
|
||||
### 视频预览
|
||||
|
||||
### 文本预览
|
||||
|
||||
### 音频预览
|
||||
|
||||
### PDF 预览
|
||||
|
||||
### Office 预览
|
||||
|
||||
### 3d 文件预览
|
||||
|
||||
### 生成直链
|
||||
|
||||
### 页面设置
|
||||

|
||||
### 后台设置-登录
|
||||
|
||||
### 后台设置-存储源列表
|
||||
|
||||
### 后台设置-存储源权限控制
|
||||
|
||||
### 后台设置-添加存储源(本地存储)
|
||||
|
||||
### 后台设置-添加存储源(世纪互联)
|
||||
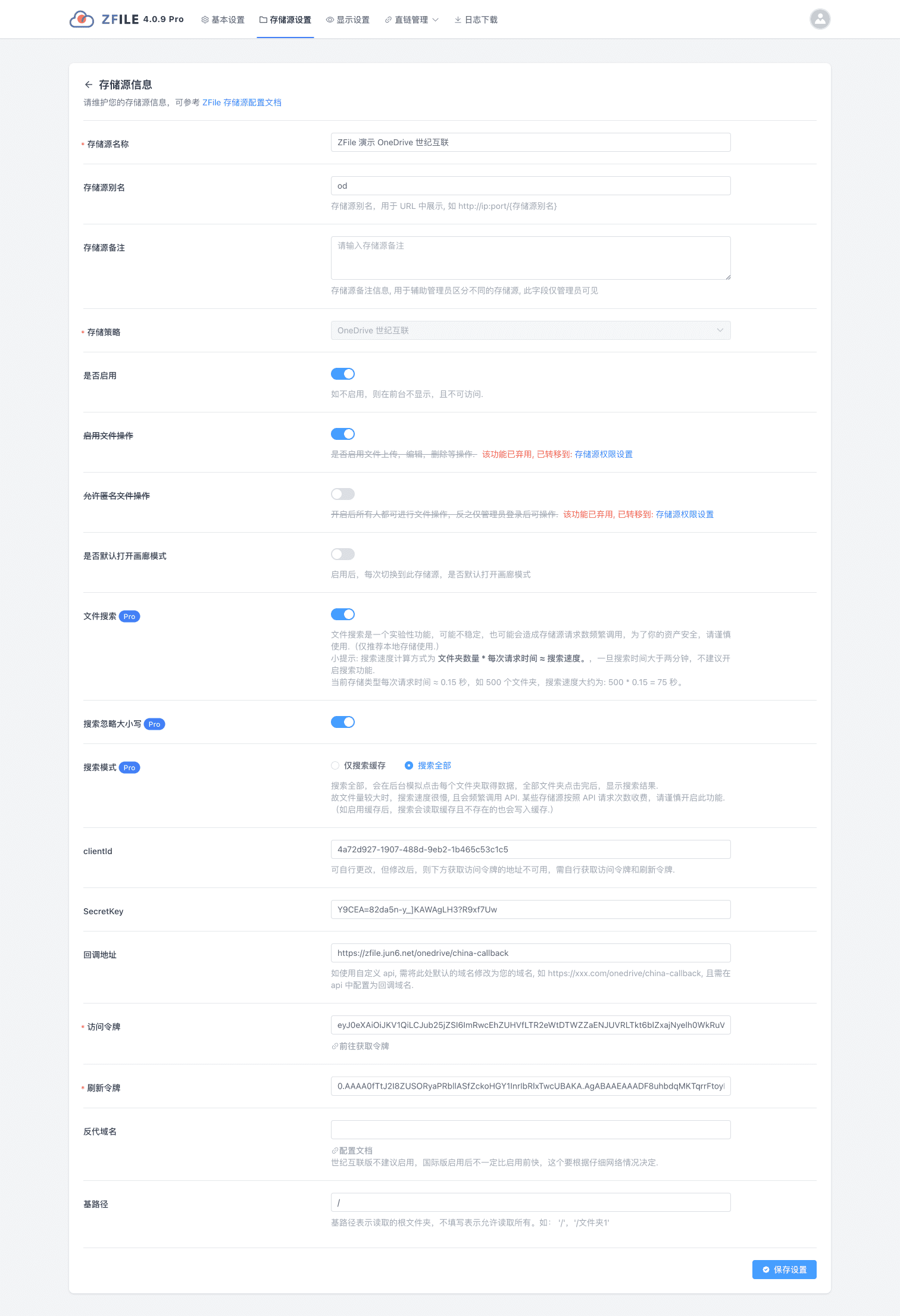
|
||||
### 后台设置-显示设置
|
||||
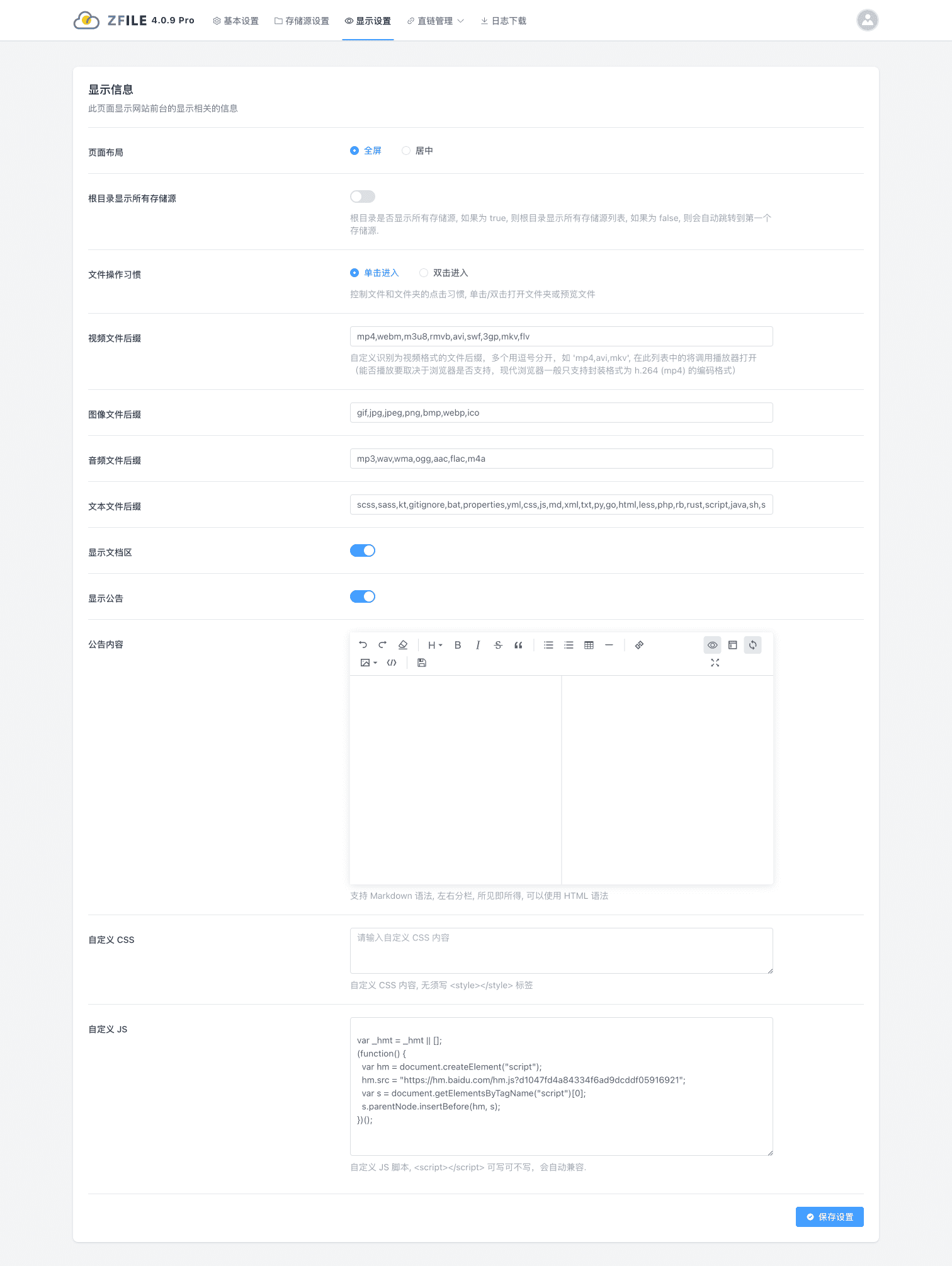
|
||||
|
||||
|
||||
## 支持作者
|
||||
|
||||
如果本项目对你有帮助,请作者喝杯咖啡吧。
|
||||
|
||||
<img src="https://cdn.jun6.net/2021/03/27/152704e91f13d.png" width="400" alt="赞助我">
|
||||
|
||||
## Status
|
||||
|
||||

|
||||
|
||||
## Star History
|
||||
|
||||
[](https://star-history.com/#zfile-dev/zfile&Date)
|
||||
20
apps/zfile/data.yml
Normal file
@ -0,0 +1,20 @@
|
||||
name: ZFile
|
||||
tags:
|
||||
- 工具
|
||||
title: 基于 Java 的在线网盘程序
|
||||
type: 工具
|
||||
description: 基于 Java 的在线网盘程序
|
||||
additionalProperties:
|
||||
key: zfile
|
||||
name: ZFile
|
||||
tags:
|
||||
- Tool
|
||||
shortDescZh: 基于 Java 的在线网盘程序
|
||||
shortDescEn: Java-based online disk program
|
||||
type: tool
|
||||
crossVersionUpdate: true
|
||||
limit: 0
|
||||
recommend: 0
|
||||
website: https://www.zfile.vip/
|
||||
github: https://github.com/zfile-dev/zfile
|
||||
document: https://docs.zfile.vip/
|
||||
BIN
apps/zfile/logo.png
Normal file
|
After Width: | Height: | Size: 5.6 KiB |